
Before a cybercriminal wants to engage in a targeted attack against a particular organization or individual, they’d like to know a few things first. That’s where OSINT comes into play.
The term OSINT is short for open source intelligence – referring to any bit of information that can be gathered by attackers for free. This is normally details collected on the Internet (e.g., company and title from LinkedIn, etc.), but, technically, can include offline information. These valuable pieces of information are collected using a variety of tools and methods that, in general, do not tip off the victim of the OSINT activity in the slightest.
The goal of any targeted attack is to make it look as legitimate as possible. This involves using as many contextual cues as are available to improve the illusion of legitimacy and lower the potential victim’s defenses. While I’ve given two examples of OSINT that can easily be collected, curiosity normally drives most security professionals to wonder what other kinds of details are relatively simple to find.
The OSINT Framework is a visually-represented collection of what data is able to be collected and by which tools.
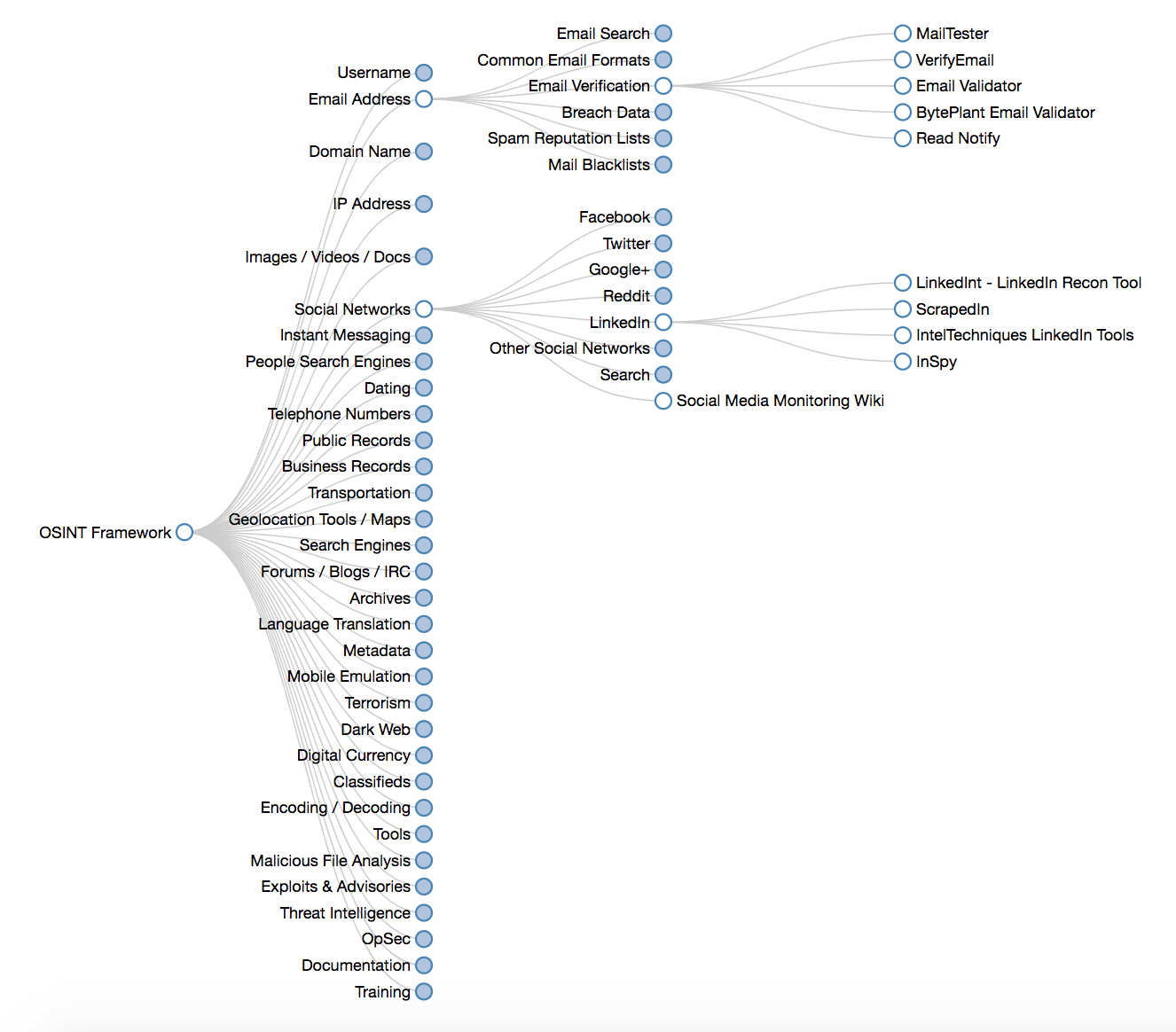
Many of these tools fall into the category of penetration testing toolsets used by red teams. Should you want to do a bit more diligence into what these tools can do and how they are used, there are a few places to look:
- Kali Tools – based on the Kali Linux penetration testing distribution, this site provides information on each tool and how to use it.
- Searx – a metasearch engine, this site gives you search results from over 70 search engines anonymously.
 If you’d like to hear more about the topic of OSINT, check out our latest on-demand webinar A Look Behind The Curtain: Open Source Intelligence (OSINT) Hacking Data Sources That Bad Guys Use, featuring world-renowned hacker Kevin Mitnick. Get an inside look into some of Kevin’s most prized, underground OSINT secrets and how the bad guys use those techniques to target your users and your organizations.
If you’d like to hear more about the topic of OSINT, check out our latest on-demand webinar A Look Behind The Curtain: Open Source Intelligence (OSINT) Hacking Data Sources That Bad Guys Use, featuring world-renowned hacker Kevin Mitnick. Get an inside look into some of Kevin’s most prized, underground OSINT secrets and how the bad guys use those techniques to target your users and your organizations.
Don't like to click on redirected buttons? Copy & paste this link into your browser:





