According to McAfee’s Advanced Threat Research team and McAfee Labs Malware Operations Group, a new global campaign is underway, targeting key industries, potentially for espionage purposes.
In a recent report from antivirus firm McAfee, a new campaign is showing signs of going global, demonstrating a concerted effort to hit organizations in industries including nuclear, defense, energy and financial groups. Dubbed “Operation Sharpshooter,” malicious source code is implanted into endpoint using a phishing attack disguised as legitimate industry job recruitment activity.
The malicious code, referred to as Rising Sun has source code that links it back to the Lazarus Group – a cybercriminal organization believed to be based out of North Korea that was responsible for the 2014 cyberattack against Sony Pictures Entertainment.
Rising Sun uses a 2015 backdoor Trojan – Duuzer – which is used to gain full control of computers, giving attackers the ability to:
- Gather system and drive information
- Create, enumerate, and end processes
- Access, modify, and delete files
- Upload and download files
- Change the time attributes of files
- Execute commands
- And more
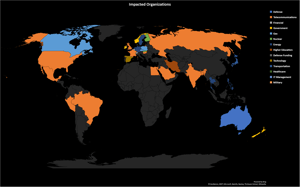
In October and November of this year, McAfee has seen Rising Sun in 87 organizations across the globe, predominantly in the United States.
The use of a recruitment phishing scam and the targeted nature of the attack should put even those organizations not in industries supporting critical infrastructure on edge. The targeted nature of attacks today means cybercriminals are keenly aware of your industry vertical, the potential ways to make money, the context needed to trick users into clicking on malicious documents, and are doing diligence on who’s who within targeted organizations at this very moment.
At the root of nearly every successful scam targeting organizations is a user responding to an email received. Whether a solicitation from a supposed recruiter or a request to reset a password, the bad guys know how to get users to respond.So, organizations need to protect themselves by educating users with Security Awareness Training, elevating the users understanding of the state of social engineering, how they are the target, and how to avoid becoming a victim.






