The context of contacting the victim via a credible website may be all that was needed to trick one job seeker into installing malware on the network of a bank.
Imagine you’re on LinkedIn and you see an ad for an open position that you’re perfect for. See anything wrong with that? Given you’re on a website that knows your job title, industry sector, location, etc. I’d say none of us would give it a second thought and assume it was legitimate.
That was exactly what hackers were hoping for when they used LinkedIn ads to target employees of the victim bank (which include company as a part of their ad filtering). A bank employee responded to an ad seeking a developer position. The employee was contacted and even had a call with the would-be employer via Skype.
All this social engineering was in place to lower the employee’s defenses when the actual attack occurred – the cybercriminals asked him to install a program (ApplicationPDF.exe) that would generate his online application. The program didn’t trigger any alarms on the bank's antivirus (and, from the look of the article, nor the potential “applicant”).
The thinking is that hackers were attempting to gain entry to the bank’s network in an attempt to reach applications that control ATMs and debit cards.
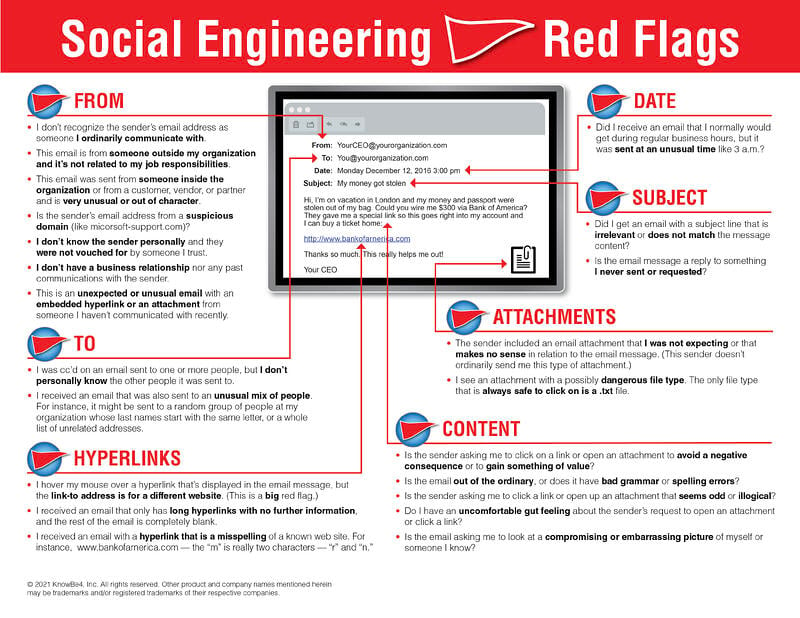
We often see employees as the weakest link in cybersecurity; as if they are simply careless. But stories like this prove that anyone can fall prey to a scam. It’s the very reason why every employee – from the lowest in the ranks to the highest – should go through Security Awareness Training to elevate their understanding of how these scams unfold (regardless of how credible they appear) and how to spot them (hint: the PDF application was the big red flag in this scam).