 Negligent employees remain the number one cause of data breaches at small businesses across America. So why do small businesses continue to struggle with good cyber security practices and what can they do to correct those habits?
Negligent employees remain the number one cause of data breaches at small businesses across America. So why do small businesses continue to struggle with good cyber security practices and what can they do to correct those habits?
Small to medium-sized businesses are hit with nearly 4,000 cyber attacks per day -- and that number is only expected to grow, according to a new report. Small businesses are even more likely to be targeted by malicious hackers, but the actions of small business employees and leaders reveal little is actually being done to address the negligence towards security.
Chicago, IL-based IT consultancy for SMBs, Switchfast surveyed over 600 small business leaders - VPs to the C-suite - and small business employees about their cyber security habits.
It wanted to discover how employee behaviors contribute to the rising number of cyber attacks against small businesses - and how companies can begin to address poor cyber hygiene and mitigate risk.
Cyber attacks have huge consequences for business. The survey found that three out of five (60 percent) of small businesses that suffered a breach are likely to go out of business within six months.
Unfortunately, small businesses take risks in relying on their employees to not fall victim to lurking hackers. They do not have the manpower that enterprises have to handle things like IT and security.
They do not prioritize security education and best practices: Thirty-five percent of employees, and 51 percent of leaders are convinced their business is not a target for cybercriminals.
This relaxed attitude towards cyber threats, often leads to reactive policies that cannot mitigate damage when disaster strikes.
The survey found that two-thirds (66 percent) of SMB leaders connect to public Wi-Fi for work, while 44 percent of SMB employees do the same. Connecting to a Wi-Fi hotspot at a coffee shop or hotel lobby, can cause immense damage to a small business.
Hackers can launch man-in the-middle attacks or distribute malware when users connect to private servers over open Wi-fi networks.
Over three out of five (62 percent) of leaders and managers use their work computer to access social media accounts, while only 44 percent of employees do this.
Encouraging employees to bring their own device into work means that businesses can implement filtering software to control what content is viewed on their network. This could protect companies from sites carrying malicious payloads like malware, Trojan horses and spyware.
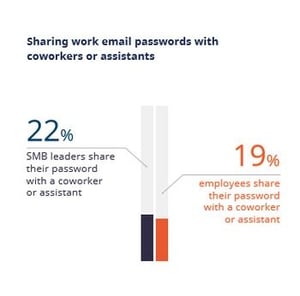
One in five (22 percent) of leaders and 19 percent of employees share their email password with co-workers or assistants. Collaboration software, delegate access and shared storage means that employees should never need to do this.
Educating employees is paramount to ensure that employee's habits do not leave vulnerabilities in an organization's defenses that could be easily exploited by hackers. Full Story at ZDNet: https://www.zdnet.com/article/one-in-five-employees-share-their-email-password-with-co-workers/
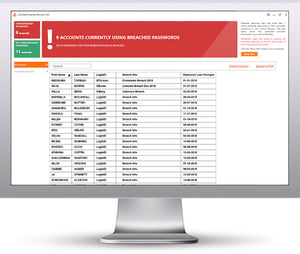 KnowBe4’s Breached Password Test (BPT) checks to see if your users are currently using passwords that are in publicly available breaches associated with your domain. BPT checks against your Active Directory and reports compromised passwords in use right now so that you can take action immediately!
KnowBe4’s Breached Password Test (BPT) checks to see if your users are currently using passwords that are in publicly available breaches associated with your domain. BPT checks against your Active Directory and reports compromised passwords in use right now so that you can take action immediately!
Here’s how Breached Password Test works:
- Checks to see if your company domains have been part of a data breach that included passwords
- Checks to see if any of those breached passwords are currently in use in your Active Directory
- Does not show/report on the actual passwords of accounts
- Just download the install and run it
- Results in a few minutes!
Find out now which users are using hacked passwords:
PS: Don't like to click on redirected buttons? Cut & Paste this link in your browser:





