A new campaign spotted in the wild uses a tried-and-true method of convincing victims to provide their Office 365 logon credentials to be used in future attacks.
Security researchers at MailGuard have identified a new realistic-looking campaign that notifies users of “spam” messages with subject lines made to look important. This technique is designed to mimic Microsoft’s own security safeguards and could confuse would-be victims into retrieving the nonexistent email message.
The phishing notification is rather convincing and impersonates Microsoft rather well:
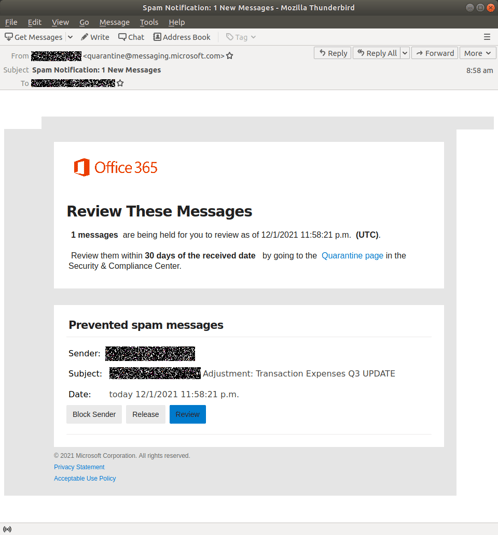
One small note about the campaign that I find particularly brilliant is the fact that the page users are taken to in order to provide their Office 365 credentials states “Session Expired”. It’s a small nuance that establishes why the user must enter their credentials. Most attacks like this simply ask for credentials with no explanation as to why users aren’t taken directly to the email in question (as would be expected).
Microsoft has been the primary impersonated brand by phishing attacks for many quarters, being leveraged in nearly one-third (29%) of phishing attacks using brand impersonation – something I suspect will continue for the foreseeable future, given Microsoft’s hold on the digital workspace market.
Organizations utilizing Microsoft’s Office 365 services should educate users of such campaigns using Security Awareness Training to minimize the risk of successful attack.
 Here's how it works:
Here's how it works:




