 A new highly-targeted phishing campaign is seeking to compromise the online credentials of those with influence within an organization using an Office 365-themed update attack.
A new highly-targeted phishing campaign is seeking to compromise the online credentials of those with influence within an organization using an Office 365-themed update attack.
The bad guys used to try to con anyone with the organization they could and then work to swim “upstream” to compromise someone in IT, an executive, etc. These days, the bad guys are dialed into using online tools like LinkedIn to identify their targets and work by using social engineering tactics to convince their victims into giving up valuable credentials.
In a new attack spotted by security vendor Area 1 targets financial departments, C-suite executives and executive assistants within the financial services, insurance and retail industries.
Using an Office 365 service update phishing email as the initial attack vector, prospective victims are encouraged to open the attachment to read about an important update. The attachment can be a PDF, HTML or HTM file.
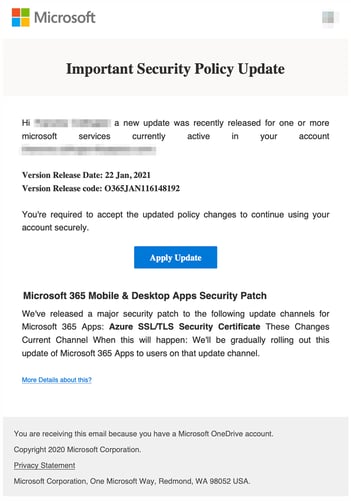
Source: Area 1
A JavaScript “unescape” command is used to obfuscate the HTML that loads a phishing kit-based Office 365 credential harvesting site. The phishing kit even includes a very realistic touch of popping up an updated privacy policy before allowing the user to continue.
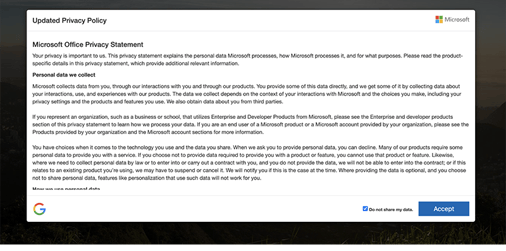
Source: Area 1
All this works to lower the victim’s defenses, establish credibility, and increase the chance of attack success.
Teaching users via Security Awareness Training to watch out for abnormal communications (such as “Microsoft” using an attachment to convey update details) can stop attacks like these in their tracks, no matter how convincing their phishing kit is.
 Here's how it works:
Here's how it works:




