 When push-based multifactor authentication (MFA) first came out, I was a big fan. I promoted it as a strong and safe MFA option in my book, Hacking Multifactor Authentication. That was before I realized that a non-small percentage of users would willingly approve logins they otherwise had nothing to do with, once again undermining the best intentions of the latest technology with unexpected human behavior. This is the unstoppable, repeatable story of cybersecurity.
When push-based multifactor authentication (MFA) first came out, I was a big fan. I promoted it as a strong and safe MFA option in my book, Hacking Multifactor Authentication. That was before I realized that a non-small percentage of users would willingly approve logins they otherwise had nothing to do with, once again undermining the best intentions of the latest technology with unexpected human behavior. This is the unstoppable, repeatable story of cybersecurity.
Since then, I have written a lot about push-based MFA, how it works, and the good and bad of it, how to improve it, including here:
- Making Better Push-Based MFA
- Safety of Push-Based MFA Being Shredded by End Users
- If You Use Push-Based MFA, Did You Do This?
- Making Better Push-Based MFA
- Weak vs. Strong Push Notifications
Push-Based MFA
Push-based MFA sends an approval message to a user’s device, usually a cell phone, which they must manually approve in order to successfully log into push-based-protected sites. The push-based message is often sent via SMS text or to a phone-based/device-based app (see Google example below).
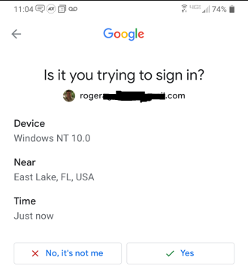
Number Match MFA Solution
In April of this year, I wrote about a new feature, generally known as “number matching MFA” that promised to improve the security of push-based authentication. Originally, implemented as part of Microsoft’s and Google’s push-based MFA “beta” features, Duo Security and other vendors also have it or plan to add it as a feature.
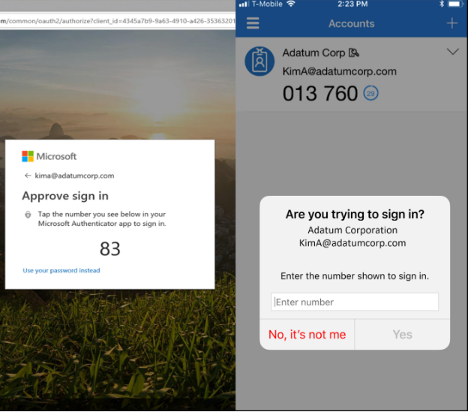
In a nutshell, number match changes the push-based-protected login screen to display a number, usually two digits between one and 99, during a login. The user getting a push-based login message to review, must know the number and type it or correctly select it on the push-based login approval screen, to be able to approve the involved login.
Here is an example (shown below) from Microsoft:
Some solutions ask the user to select the right number instead of typing it in (example from Google shown below).
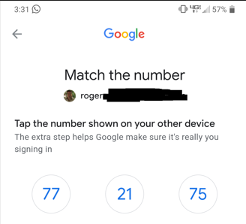
The latter message is probably going to have less errors because there is less of a chance for a user to type in the wrong digits and it only takes one action instead three (as indicated in the former example). The second example’s GUI is better. Less user friction.
The number match increases the odds that the user involved in approving the login has actually seen the login screen during the related login attempt.
It is a good idea. Even CISA has come out to support number matching push-based MFA.
While it is a good idea, it is not a perfect idea. If you have or plan to implement push-based MFA, you should enable this feature if it is available. But it does not stop all of the attacks against push-based MFA. If you think it does, you will likely end up hacked.
Number matching increases the odds that the approver is sitting in front of the login screen, but it does not guarantee it. Many of the most notorious hacks involving push-based MFA have occurred because the attacker called the victim, pretending to be from IT, and told the victim they needed to approve the login. That attacker can just as easily add, “And the number match is 21.” If the victim is incentivized and going to approve the fraudulent login anyway, why would number match stop them from a determined adversary who is social engineering them over the phone?
Number matching will prevent a user from approving a bunch of unexpected prompts, at least without having to have someone tell them the number or from seeing it themselves. I am not sure how much of push-based MFA phishing involves just the login prompt appearing versus the victim being contacted by the attacker, but it is bound to be a lower percentage of the latter. How much lower? It is anyone’s guess. But if I had to guess, I bet number matching would put down 50% to 75% of push-based MFA attacks. That is pretty good. But that means 25% to 50% of attacks will still succeed.
I expect as number matching becomes more the norm in the push-based MFA world, that hackers will simply adapt. The hackers who never used to worry about and work around number matching will simply start doing so. And therefore, the amount of protection provided by number matching will decrease over time. Still, it helps a lot, and so, you should enable it. It is just not perfect.
MFA Hacking Defense
Do you know what is better? What would work close to 100% of the time?
Education.
As you hand out push-based MFA to your users, educate them about the common types of attacks against push-based MFA, whether number matching is enabled or not. Tell them that you and no one working for your organization will ever ask them to approve a prompt that they themselves, the user, did not initiate. Tell them that legitimate IT will never contact them and ask them to approve a problem. Tell them that if anyone contacts them and claims to have the authority to force them to approve a login that they themselves, the potential victim, did not initiate, that they are allowed…no…required…to deny that login request. And then they should immediately contact IT/IT Security to report the possible breach attempt. Tell them that there is no plausible scenario where they will be asked to approve a login that they themselves did not initiate. It works better than a number match.
A little education goes a long way. New-school security awareness training can enable your employees to thwart evolving MFA-based attacks.
 Here's how MASA works:
Here's how MASA works:




