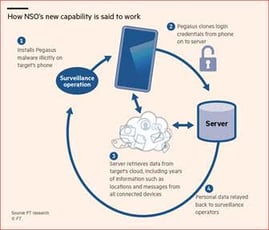
The Israeli company whose spyware hacked WhatsApp has told buyers its technology can surreptitiously scrape all of an individual’s data from the servers of Apple, Google, Facebook, Amazon and Microsoft, according to people familiar with its sales pitch.
NSO Group’s flagship smartphone malware, nicknamed Pegasus, has for years been used by spy agencies and governments to harvest data from targeted individuals’ smartphones.
But it has now evolved to capture the much greater trove of information stored beyond the phone in the cloud, such as a full history of a target’s location data, archived messages or photos, according to people who shared documents with the Financial Times and described a recent product demonstration.
The new technique is said to copy the authentication keys of services such as Google Drive, Facebook Messenger and iCloud, among others, from an infected phone, allowing a separate server to then impersonate the phone, including its location.
This grants open-ended access to the cloud data of those apps without “prompting 2-step verification or warning email on target device”, according to one sales document.
It works on any device that Pegasus can infect, including many of the latest iPhones and Android smartphones, according to the documents, and allows ongoing access to data uploaded to the cloud from laptops, tablets and phones — even if Pegasus is removed from the initially targeted smartphone.
“This has got to be a serious wake-up call for a lot of companies,” said John Scott-Railton, a senior researcher at the University of Toronto’s Citizen Lab, who has been following the use of Pegasus. He said it “accelerates the need for stronger forms of device authentication”.
It also accelerates the need to train your employees regarding the use of social media and your organization's security. Full story at the Financial Times (paywall)
Brand-New Tool: Social Media Phishing Test Checks for Users Vulnerable to Social Media Related Attacks
Phishing is still the #1 threat action used in social engineering attacks, and spear phishing, in particular, takes  advantage of your users’ socially networked lives.
advantage of your users’ socially networked lives.
Many of your users are active on social media sites like Facebook, LinkedIn, and Twitter. Attackers use social media to target both your brand, your users, and even your customers by distributing malware or using social engineering to phish for credentials. These platforms have become a goldmine for the bad guys to carry out social media phishing attacks against your organization!
Don’t get hacked by a social media phishing attack!
KnowBe4’s new Social Media Phishing Test (SPT) is a complimentary IT security tool that helps you identify which users in your organization are vulnerable to these types of phishing attacks that could put your users and organization at risk.
SPT will give you quick insights into how many users will fall victim so you can take action to train your users and better protect your organization from these social media phishing attacks!
Here’s How the Social Media Phishing Test works:
- Immediately start your test with your choice of three social media phishing templates
- Choose the corresponding landing page your users see after they click
- Show users which red flags they missed or send them to a fake login page
- Get a PDF emailed to you in 24 hours with your percentage of clicks and data entered
Find out how many of your users are vulnerable to social media related phishing attacks now! Don't like to click on redirected buttons? Copy & paste this link into your browser:
Don't like to click on redirected buttons? Copy & paste this link into your browser:
https://www.knowbe4.com/social-media-phishing-test




