 Part of a six-month attack, email accounts on the NHS’ Microsoft 365 instance were compromised, resulting in over 1,100 targeted email attacks used to obtain more credentials.
Part of a six-month attack, email accounts on the NHS’ Microsoft 365 instance were compromised, resulting in over 1,100 targeted email attacks used to obtain more credentials.
According to security researchers at email protection vendor Inky, the 139 compromised NHS accounts were being misused from October 2021 until March of 2022 as the cornerstone of further phishing attacks attempted to either harvest credentials to major online platforms, or to trick victims into providing banking details.
Emails were likely sent using two IP addresses serving as SMTP relays for the NHS’ 27,000+ users, allowing attackers to work remotely. What may have allowed this attack to remain undetected for 6 months was the number of emails being sent:
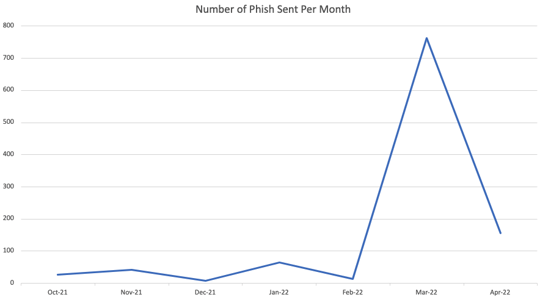
You’ll note the dramatic spike in the number of emails sent in March of this year, likely drawing attention to the attack.
Emails impersonated both the NHS and individuals within, using NHS email footers, and names of compromised individuals to add credibility to the scams.
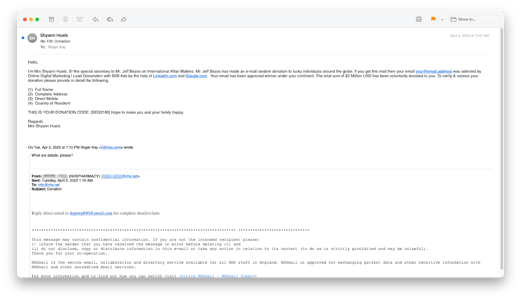
While there were only 139 compromised email accounts (out of over 27,000, according to the NHS), it literally only takes a single phishing email to alter the course of an individual or an organization. Because most phishing scams need to get the victim to focus on one response action (e.g., clicking a link or opening an attachment), the scams can generally be identified pretty easily, if the user is vigilant.
And this vigilance comes with education through Security Awareness Training designed to help users understand the nature of phishing attacks, social engineering techniques, and the role they play in corporate cybersecurity.
 Here's how it works:
Here's how it works:




