 New details from Microsoft Security Intelligence discuss an attack that displays ransomware-like behavior, but simply seeks to install the credential theft-focused remote access trojan.
New details from Microsoft Security Intelligence discuss an attack that displays ransomware-like behavior, but simply seeks to install the credential theft-focused remote access trojan.
Last week, Microsoft spotted a new attack using the year-old Java RAT, STRAAT, in the wild. Starting as a phishing attack sent under the premise of containing a list of outbound payments made by your company, this attack uses a PDF that connects to an attacker-controlled domain to download and install the STRAAT malware.
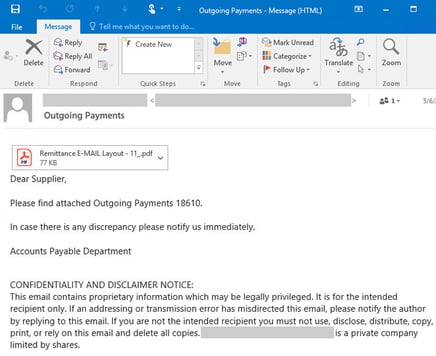
Source: Microsoft
The multi-faceted malware can be used to collect passwords from browsers and applications including Firefox, Internet Explorer, Chrome, Foxmail, Outlook, and Thunderbird. It also captures keystrokes and can run remote commands and launch PowerShell scripts on the infected endpoint.
Microsoft Security Intelligence noted on Twitter that the current version of the malware is “notably more obfuscated and modular than previous versions, but the backdoor functions mostly remain the same” implying the author is working to improve the efficacy of the malware.
Users need to be aware to simply not engage with unsolicited emails that have little or nothing to do with their job. And even if, in this case, the recipient is in the Accounts Payable department, they should pay close attention to the sender’s email address to make certain your company does business with theirs before opening.
This kind of vigilant behavior is achieved by organizations that employ continual Security Awareness Training, keeping used updated on the latest scams, themes, and social engineering tactics used in phishing attacks.
 Here's how it works:
Here's how it works:




