Here is a ransomware horror story for you...
An obscure 2-year old ransomware strain called Virlock has a nasty feature: it is capable of stealthily spreading itself via cloud storage and collaboration apps. That way just one infected user can unknowingly spread the infection further across your network, Netskope researchers discovered. Virlock is borrowing from a wide range of threat techniques.
How does it work?
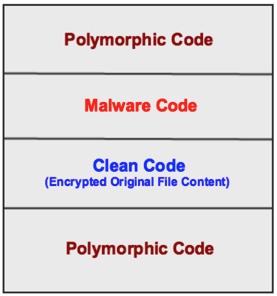 Ransomware normally spreads through email phishing attacks, exploit kits, removable drives or external network shares. However, Virlock is a weird family of ransomware that not only encrypts files but also converts them into a polymorphic file infector just like a virus. Apart from infecting the usual documents and image related files, it also infects binary files. Yikes.
Ransomware normally spreads through email phishing attacks, exploit kits, removable drives or external network shares. However, Virlock is a weird family of ransomware that not only encrypts files but also converts them into a polymorphic file infector just like a virus. Apart from infecting the usual documents and image related files, it also infects binary files. Yikes.
Here is an example of how it spreads
In short: User A and User B are collaborating through the cloud storage app Box, using a folder called "Important". Both users have some of the files within the folder synced to their own machine.
User A falls for a social engineering attack and gets infected with Virlock ransomware on their own machine, encrypting all their files and at the same time turning them into new Virlock infector files, including the files which are synced on Box. So, Virlock also spreads to the cloud folder and infects the files stored there, which in turn get synced to User B's machine.
Now, User B clicks on any of the files in the shared folder on their box, the infected Virlock file is executed and the rest of the files on the machine of User B become infected and in their turn becoming Virlock file infectors just like a virus. Here are the blow-by-blow screenshots, courtesy Netskope.
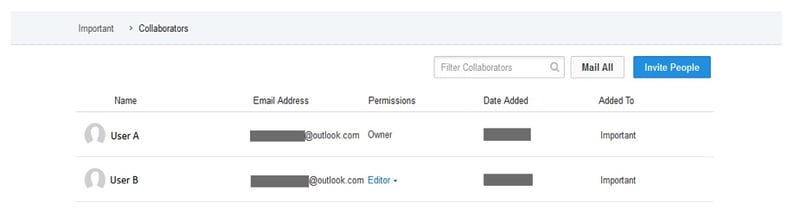
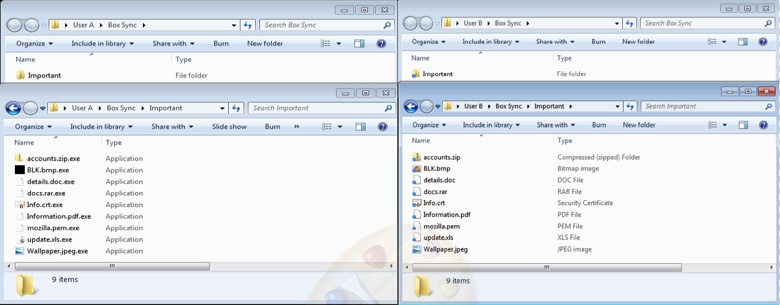
This “Important” folder has few files that both User A and User B have synced on their respective machines as shown here:
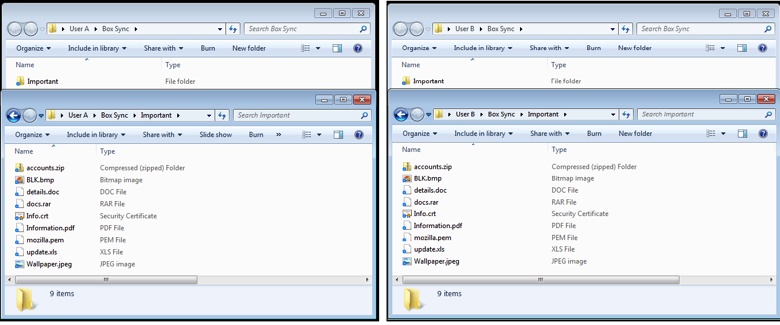
User A gets infected with Virlock ransomware. User A’s files are all encrypted and turn in to Virlock infector files. As part of encrypting all the files on User A’s machine, the files within the Box Sync “Important” folder are also encrypted and turn into Virlock infector files as shown here:
The Box sync client on User A’s machine will sync the files to the cloud as shown here:
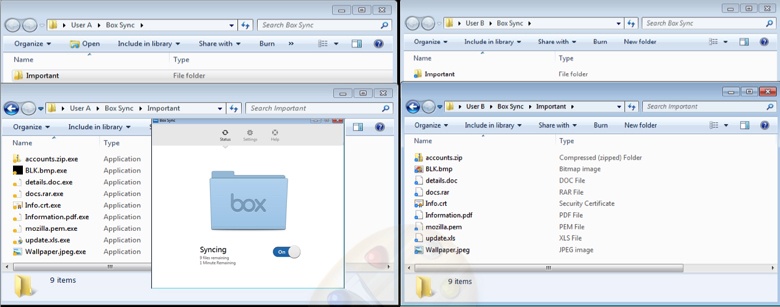
As the “Important” folder is also shared with User B, the files within “Important” folder are synced to User B’s machine Box sync folder as shown here:
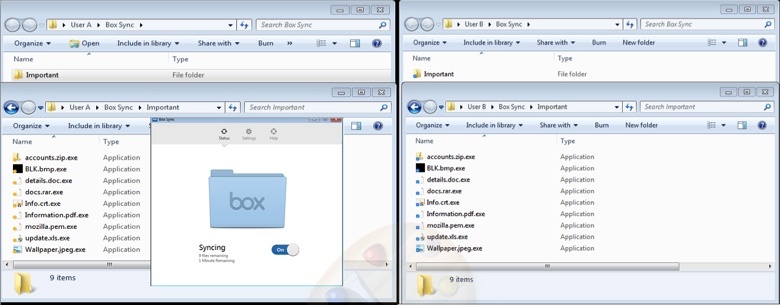
The above scenario is not just limited to User A and User B and will extend to all the users of an enterprise who are collaborating with each other. Consider the User-File collaboration graph below of a typical enterprise with users (in black dots) and the files (in blue dots). All the users within the red boundary might get infected with Virlock ransomware due to fan-out effect within minutes.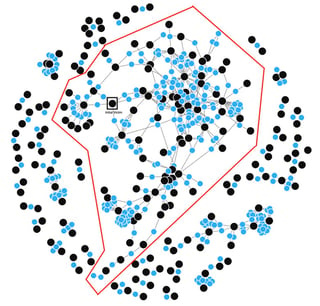
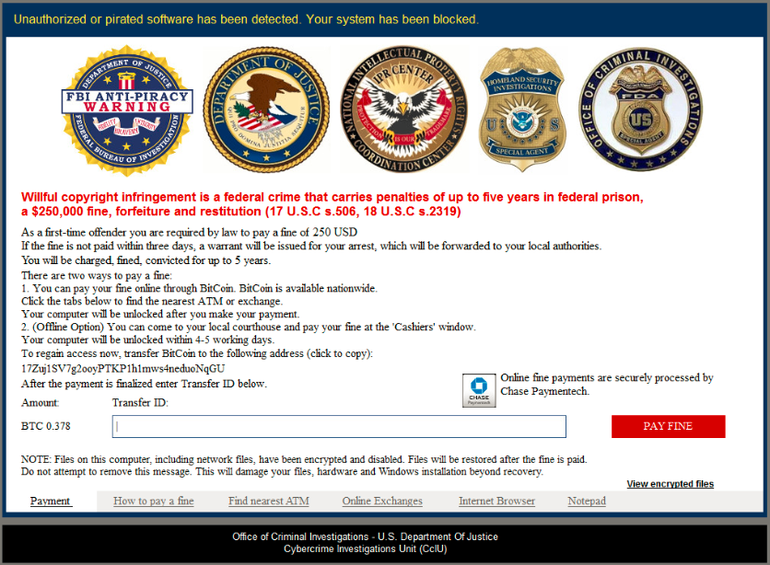
And another weird twist, it claims to be an FBI fine for piracy
Like all other ransomware strains, Virlock asks the victim for a payment in Bitcoin in order to release their machine. However, unlike modern strains such as Cerber or Locky that blatantly stated the victim's files have been taken hostage, Virlock positions itself as an anti-piracy warning from the FBI.
The claim is that pirated software has been found on their machine and threatens them with prison and a $250,000 fine if they don't pay a $250 'first-time offender' fine. This is a tried-and-true social engineering tactic that has been used by cybercriminals for years in an effort to spook victims into paying up quickly.
Silver lining: Virlock "encryption" is not technically accurate
Netskope is claiming that Virlock "encrypts" files before infecting them with its polymorphic code. "Encrypts," however, is a bit of a strong word, and not really technically accurate. Virlock uses a so-called XOR and XOR-ROL scheme to "scramble" or "obfuscate" files.
Both procedures are reversible (if you know what you're dealing with). Real crypto-ransomware uses a combination of AES and RSA crypto algorithms to truly encrypt your files -- and there is no reversing of files encrypted that way unless the bad guys leave the private key lying around somewhere by mistake ( it has happened).
 The bad guys using Virlock as a ransomware vehicle have a problem, the very strength of this ransomware strain (potentially massive propagation) also becomes its weak point.
The bad guys using Virlock as a ransomware vehicle have a problem, the very strength of this ransomware strain (potentially massive propagation) also becomes its weak point. 
You need a ransomware/virus infection spreading on your network like a hole in the head. If you want to spend less time putting out fires, get more time to be proactive, and get the things done you know really need to be done, step employees through new-school security awareness training. It will help you prevent this kind of disaster or at least make it very hard for the bad guys to social engineer your employees.
Find out how affordable this is for your organization. Get a quote now so you can deploy in Q4:





