The decade-old malware traditionally used to capture banking details has been given new life and spotted in the wild, being distributed via malicious Word documents.
A number of new variants of the Ursnif malware have popped up over the last few years since the release of the source code online, allowing developers to customize the code to steal online credentials.
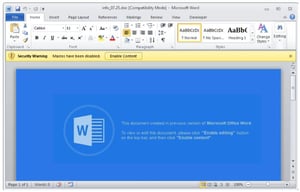
New research from security vendor Fortinet shows Ursnif is being distributed via phishing emails containing a malicious Word document. Using the simple social engineering tactic of the Word doc claiming the document was created in a previous version of Word and requires the user to enable macros to view it, cybercriminals are tricking users into enabling macros. Once enabled, malicious VBA code downloads and drops Ursnif onto the unsuspecting computer.
Social Engineering tactics are betting on the human element to be the weakest link in your security strategy; if the user can be fooled into acting in accordance with the attackers wishes, the user goes from being a part of your security strategy to part of the attack.
Users can be easily taught to avoid enabling macros in Office documents, as well as educated on phishing tactics used to attempt to trick them by putting them through continual Security Awareness Training. Attackers most often require the help of the user at some point in an attack. By training users on what to look for, stopping attacks can be as simple as ignoring and deleting an email.
 Here's how it works:
Here's how it works:




