 Delivering an equally new Royal ransomware, this threat group monitored by Microsoft Security Threat Intelligence has already shown signs of impressive innovation to trick victims.
Delivering an equally new Royal ransomware, this threat group monitored by Microsoft Security Threat Intelligence has already shown signs of impressive innovation to trick victims.
Microsoft keeps track of new threat groups, giving them a DEV-#### designation to track them until there is confidence around who is behind the group. In the case of DEV-0569, this threat group uses malvertising, and malicious phishing links that point to a malware downloader under the guise of being a legitimate software installers or software update, using spam emails, fake forum pages, and blog comments as initial contact points with potential victims.
According to Microsoft, the group has expanded its social engineering techniques to improve their delivery of malware, including delivering phishing links via contact forms on the targeted organizations’ website and hosting fake installer files on legitimate-looking software download sites and legitimate repositories to make malicious downloads look authentic to their targets.
Take the example below, where the threat group hosted their malicious downloader, known as BATLOADER, on a site that appears to be a TeamViewer download site.
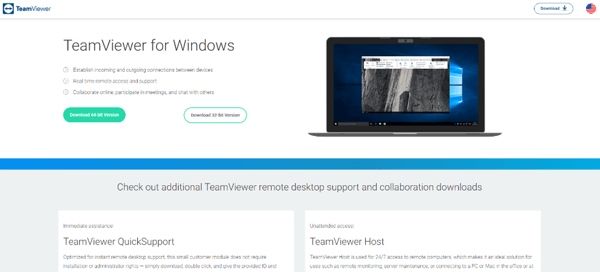
Source: Microsoft
Microsoft have also noted the expansion of their malvertising technique to include Google Ads in one of their campaigns, establishing legitimacy and blending in with normal ad traffic.
This level of innovation shows that threat actors are stepping up their game to establish legitimacy in any way possible – including paying for ads – so that victim’s defenses are down. It’s all the more reason for organizations to educate their users through Security Awareness Training to always be watchful, even in situations where everything seems “normal”; as that legitimate search query on Google could result in enabling malicious activity.
 Here's how it works:
Here's how it works:




