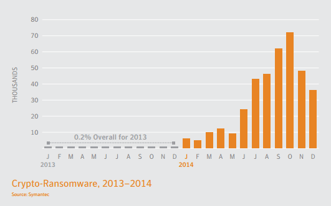
 The new Internet Security Threat report from Symantec shows that the growth of file-encrypting ransomware expanded from 8,274 in 2013 to 373,342 in 2014. This is 45 times more crypto-ransomware in the threat landscape within a one-year span.
The new Internet Security Threat report from Symantec shows that the growth of file-encrypting ransomware expanded from 8,274 in 2013 to 373,342 in 2014. This is 45 times more crypto-ransomware in the threat landscape within a one-year span.
Combine that with the new Verizon Breach Investigations Report last week which showed that you’ve got one minute and 20 seconds to save your files from being encrypted and you see the problem.
Verizon calculated 80 seconds is median time it takes for an employee to open a phishing email that lands on a company’s network and in their inbox. TeslaCrypt is one of the latest copycat ransomware strains that has ripped off the CryptoLocker brand, and is now infecting user's workstations through multiple exploit kits.
Apart from a laundry list of file types that ransomware normally encrypts, TeslaCrypt also tries to cash in on the $81 billion game market and encrypts over 40 file types associated with popular computer video games, like Call of Duty, Minecraft, and World of Warcraft as well as files related to/from iTunes. In other words: "all your files belong to us".
Instead of phishing attacks with attachments, the TeslaCrypt strain uses multiple exploit kits. An exploit kit (EK) is crimeware that gets sold on the dark web, and allows cyber gangs to infect legit websites. The workstation of the employee who clicks through to or visits that website gets exploited when it is not updated with the latest patches.
TeslaCrypt started out with the Angler EK, but recently also the Sweet Orange and Nuclear EKs. The Nuclear kit is used in a campaign right now. Potential victims are being redirected to compromised Wordpress sites that have this EK installed.
Brad Duncan, security researcher at Rackspace observed in one case that the kit successfully exploited a vulnerability in an out-of-date version of Flash player (13.0.0.182).
Once the workstation is infected, the delivered ransomware still uses the CryptoLocker branding. However, when the victim visits the payment site that instructs them on how to pay the ransom, it becomes obvious you are dealing with TeslaCrypt, which is the screen shot you see.
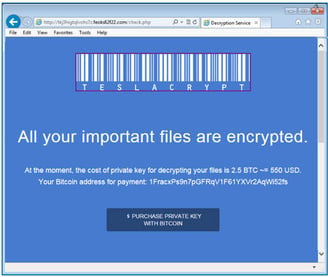
The payment process is run through a website located in the TOR domain. Each instance of the ransomware has its own Bitcoin BTC address. The files are encrypted by using the AES cipher, and encrypted files gain the .ecc extension.
What To Do About It
1) The rule "Patch Early, Patch Often" still applies, but these days, better to "Patch Now" all workstations for both OS fixes and popular third party apps that are part of you standard image rolled out to end-users. A (free) product like Secunia can scan for unpatched third party apps.
2) Make sure your Backup/Restore procedures are in place. Regularly TEST, TEST, TEST if your restore function actually works. The latter is often overlooked.
3) The TeslaCrypt strain uses social engineering to make a user click on a link in a phishing email (It does not use email attachments). Also, this type of ransomware can use malicious ads on legit websites to infect workstations. End users need to be stepped through effective security awareness training so that they are on their toes with security top of mind when they go through their email.
Find out how affordable this is for your organization today! You will be pleasantly surprised.





