This morning, our Controller received an email from "me", stating the following:
Alanna
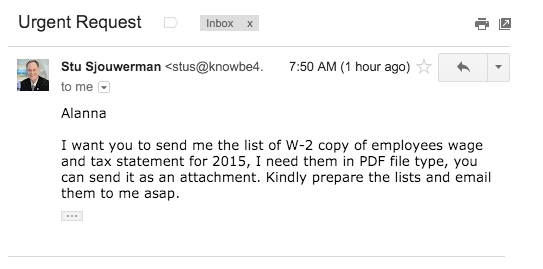
It just so happened that we have a new CFO so Alanna answered that she did not have access to that information anymore and that our new CFO could help me. Our new CFO had just stepped through all our awareness training and smelled something phishy. The two of them walked up to me and asked if I had requested a PDF with all W-2's.
Obviously I hadn't and congratulated them on a good catch. But imagine if we would have sent off those W-2's! It would have opened up our employees to identity theft because the W-2's have their full name, address, wages and social security number.
Analysis of the headers showed the hackers used someone's GoDaddy email server and the return address was definitely not me! However, it was a valid email address that the hackers were monitoring. They answered and again impersonated me. Here is the screen shot:
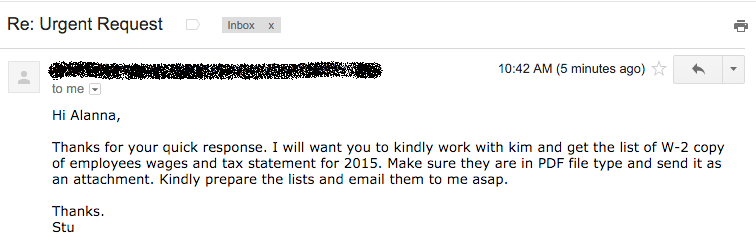
Our phishing analysts started seeing this new attack arrive on Monday through the Phish Alert Button (PAB) submissions we get from our customers.
The CFO-targeted phishes that we see through PAB submissions are almost all requested wire transfers. So, the W-2 request is a bit unusual, but the data can obviously be sold, used for identity theft and financial fraud, and mined for still more targeted phishing scams.
W-2-themed phishes have recently become quite prevalent, and organizations have been warning employees about them. See: http://vtdigger.org/2016/01/23/state-workers-w-2-info-compromised-in-phishing-scam/
But those phishes are targeted at regular employees and attempt to trick individual employees into coughing up personal info that can be exploited. The CFO-targeted phishes are a more efficient way to obtain the same data. Why bother sticking up individual victims on the street when you can simply rob the bank?
I strongly suggest you warn your Accounting and HR teams that there is a new strain of CEO Fraud asking for W-2's.
If you are a KnowBe4 customer, sending them this brand new template to inoculate them against this social engineering attack would be a really good idea. You can find the template in Phishing -> Email Templates -> System Templates -> Business -> "Urgent Request". This template has a difficulty rating of 4 out of 5, and does not have a reply email address but a link to upload the PDF to. Clicking the link presents the employee with the "oops" page.
Let's stay safe out there.




