 Beware! This new targeted attack variant of ransomware is smart, sophisticated, and does a lot more than just encrypt files.
Beware! This new targeted attack variant of ransomware is smart, sophisticated, and does a lot more than just encrypt files.
It’s inevitable that every attack vector – including ransomware – is going to evolve. In this latest iteration of the ongoing saga of bad guys encrypting your data for ransom comes SNAKE. According to MalwareHunterTeam (who first identified the variant), SNAKE ransomware has a higher level of obfuscation that normally found with ransomware – this helps to ensure the ransomware can make it past security solutions and result in a higher probability of infection.
It also works to delete Windows’ Shadow Volume copies (to eliminate the ability to easily recover), as well as kills a number of different types of processes related to security solutions, industrial control systems, remote and network management tools, and more. This can bring operations and IT support to a halt.
And, as if that wasn’t enough, SNAKE encrypts all non-OS critical files and leaves the victim with a ransom note found within a txt file:
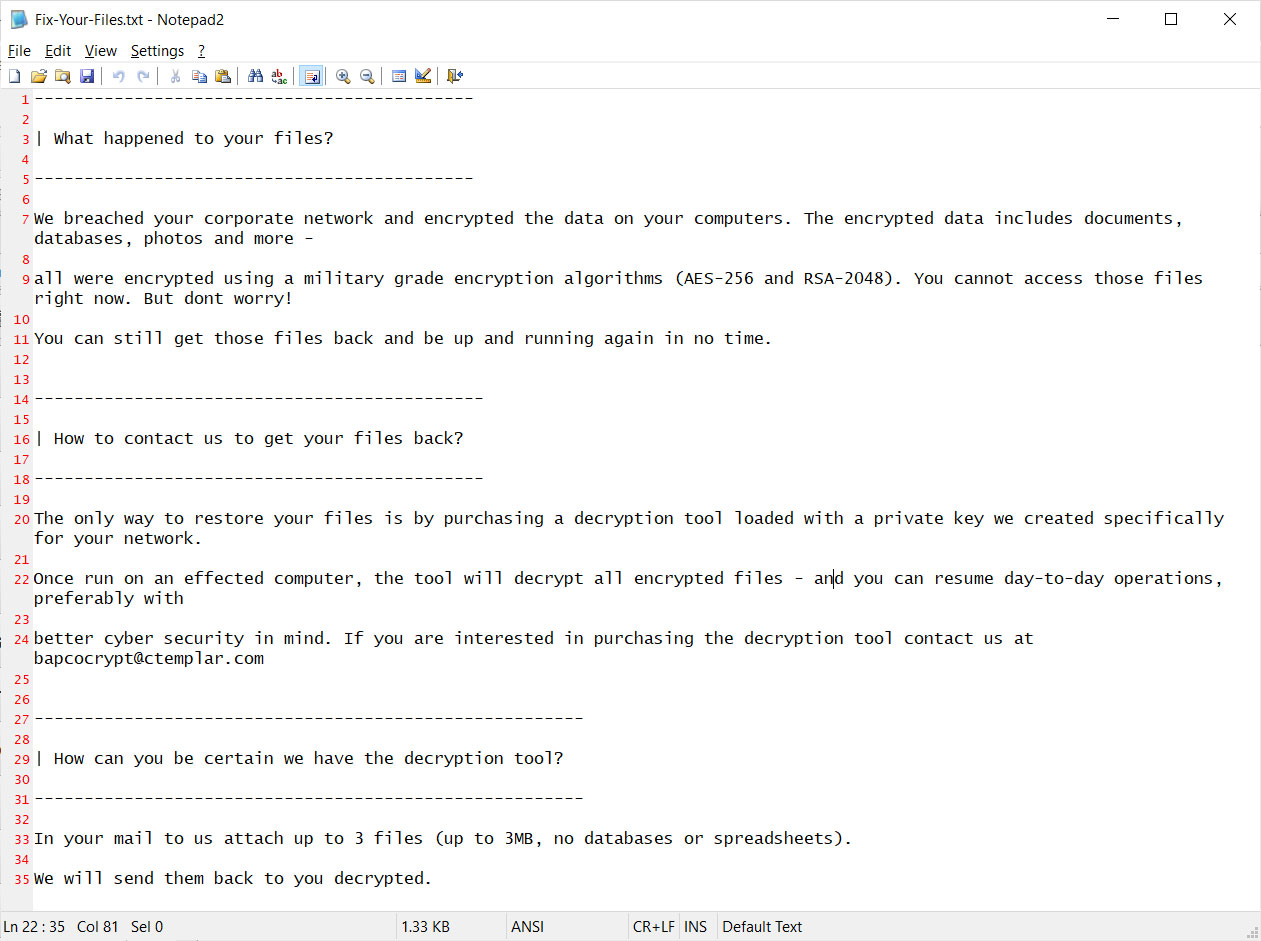
Source: Bleeping Computer
This new ransomware should come as no surprise; the bad guys are constantly watching what the good guys (read: security vendors) are doing and are taking steps to make their malware as disruptive as is humanly possible – the more disruptive, the higher and more likely the payout.
Today, ransomware usually only finds entry in one of two ways: RDP connections or email. Locking down externally-facing RDP services fixes the former, and putting users through Security Awareness Training fixes the latter. The ransomware’s focus on obfuscation as part of the attack should be a warning that simply relying on security solutions is not going to be a surefire way to protect your environment; it’s only through educating your users to spot potentially malicious emails and to not engage with them that you can avoid newer, smarter, and more deadly strains of ransomware.
 Here's how it works:
Here's how it works:




