 Focused on stealing victim credentials, this new attack uses a number of tactics to establish credibility, avoid raising red flags, and ensure they get the victim’s real credentials.
Focused on stealing victim credentials, this new attack uses a number of tactics to establish credibility, avoid raising red flags, and ensure they get the victim’s real credentials.
Security researchers at Bleeping Computer have identified a new phishing campaign that has some interesting ingenuity behind it. Sent under the premise that the potential victim has quarantined emails that need to be released by the mailbox owner, this new phishing campaign uses a from address of noreply@servicedesk.com, shown below.
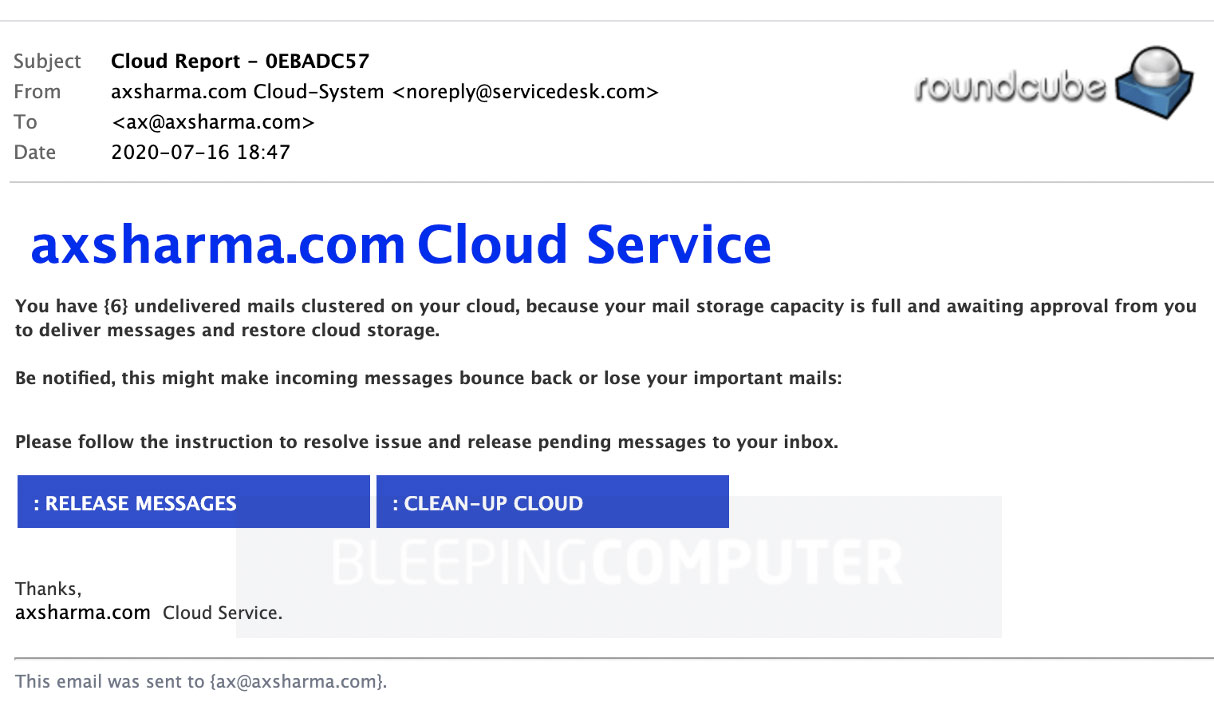
Source: Bleeping Computer
Under the hood, the use of servicedesk.com is helpful not only because it’s a term that may be familiar to a user, but also because the domain itself has no DMARC, DKIM, or SPF records to validate email senders.
Victims that click on the provided links are taken to web pages hosted on one of three enterprise cloud services – IBM Cloud, Microsoft Azure, or Microsoft Dynamics – complete with freely provided SSL certificates, all used to add credibility to links when scrutinized by security solutions.
Lastly, victims are then pushed to a spoofed logon page and are asked to authenticate. What makes this attack particularly impressive, is the authors built in password testing, so that should the victim be skeptical and put in a basic password (e.g., “12345678”), the logon page will reject the password with a “wrong password” error – again, adding legitimacy to the experience.
The bad guys are improving their understanding of the need to not just bypass security solutions, but – in essence – the user as well by creating an experience that feels “normal” to them. While the email in this case had some obvious poor choices of words and mixups of terms as obvious red flags, it still could pass for a user that isn’t paying attention. Users that undergo continual Security Awareness Training are taught to always be paying attention, skeptical of each and every email they interact with, regardless of who it’s from or what it’s about. It’s this heightened level of awareness that helps to protect organizations against phishing attacks, keeping credentials, networks, and data safe.
 Here's how it works:
Here's how it works:




