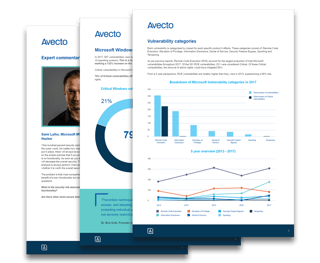
The number of Microsoft vulnerabilities has more than doubled in the last five years, according to the fifth annual Microsoft Vulnerabilities Report from Avecto.
The global security software company’s analysis of all disclosed Microsoft vulnerabilities in 2017 revealed 685 vulnerabilities, showing a significant increase compared to the number disclosed in 2013 (325).
Despite being widely regarded as the most secure Windows operating system, the number of "critical" vulnerabilities in Windows 10 rose by 64% in 2017 compared to the previous year.
In total, 587 vulnerabilities were reported across Windows Vista, Windows 7, Windows 8.1/RT 8.1 and Windows 10 operating systems in 2017. This is a record high – increasing by 132% over a five-year period.
Does removing Admin Rights help?
It was found that the removal of admin rights could mitigate 80% of all Critical Microsoft vulnerabilities reported in 2017, as well as 95% of Critical vulnerabilities found in Microsoft browsers and 60% of Critical vulnerabilities in Microsoft Office products (Excel, Word, PowerPoint, Visio, Publisher and others.)
“One hundred percent security cannot be guaranteed in the cyber world,” said Dr. Eric Cole, instructor at The SANS Institute. “No matter how many safeguards you put in place, there will always be some risk. Prevention techniques like application whitelisting, removing admin access and adopting the principles of least privilege go a long way toward protecting individual users’ machines and reducing inroads to the network while not severely restricting user functionality.”
The Upshot: Five-year analysis of Windows vulnerabilities
The most significant trends include:
- The number of reported vulnerabilities has risen 111% since 2013.
- Number of Critical vulnerabilities has risen 60% in the same period.
- There has been an 89% increase in Microsoft Office vulnerabilities and a 98% increase in Microsoft browser vulnerabilities (though this is in part due to the inclusion of Microsoft Edge from 2016 onwards.)
- Since the 2013 report, 2017 shows the largest year-on-year increase of vulnerabilities by volume, with 451 vulnerabilities reported in 2016 compared to 685 in 2017.
“Despite the continued rise in vulnerabilities impacting Microsoft software, there are actions that enterprises can take to ensure that they’re protected without sacrificing productivity,” said Mark Austin, co-founder and CEO of Avecto. “The challenges organisations face to improve security have not changed, yet many are still unaware that by simply removing admin rights, the risk of so many threats can be mitigated.”
A significant number of phishing attacks use non-patched vulnerabilities.
The best example are recent attacks like Wannacry using a newly patched microsoft hole and now cryptojacking (also known as Cryptomining) and sending phishing attacks to end-users.
Do your users know what to do when they receive a suspicious email?
Should they call the help desk, or forward it? Should they forward to IT including all headers? Delete and not report it, forfeiting a possible early warning?

KnowBe4’s Phish Alert button now also works for Gmail users with G Suite using Chrome. This gives your users a safe way to forward email threats to the security team for analysis and deletes the email from the user's inbox to prevent future exposure. All with just one click!
Best of all, there is no charge!
- Reinforces your organization's security culture
- Incident Response gets early phishing alerts from users, creating a network of “sensors”
- Email is deleted from the user's inbox to prevent future exposure
- Easy deployment via MSI file for Outlook, G Suite deployment for Gmail (Chrome)
- Supports: Outlook 2007, 2010, 2013, 2016 & Outlook for Office 365, Exchange 2013 & 2016, Chrome 54 and later (Linux, OS X and Windows)
This is a great way to better manage the problem of social engineering. Compliments of KnowBe4!
If you do not like to click on buttons with redirects, here is a link you can cut and paste into your browser: https://info.knowbe4.




