.jpg?width=400&name=iStock-1291733241%20(2).jpg) When your users receive a realistic-looking helpdesk email informing them they should update their system to prevent ransomware attacks, what could possibly go wrong?
When your users receive a realistic-looking helpdesk email informing them they should update their system to prevent ransomware attacks, what could possibly go wrong?
As we continue to hear about major companies such as Fuji Film and the world’s largest meat supplier being taken down with ransomware, the bad guys are leveraging the notoriety of these kinds of attacks as a means to create the needed urgency on the part of the phishing victim.
In a new attack spotted by anti-phishing vendor, Inky, victims are sent an email impersonating their own internal helpdesk – in some cases, complete with company branding – warning them to update their system to protect against ransomware:
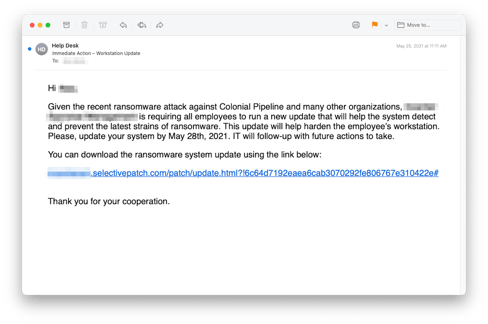
Source: Inky
Using plausible domains like selectivepatch [dot] com, the bad guys take victims to a professional-looking ransomware update page with a download named – what else? – Ransomware_Update.exe. This attack even evades detection as a malicious URL due to their use of legitimate free websites. Of course, there’s no update; the bad guys are actually downloading Cobalt Strike, a legitimate pen testing tool misused by cybercriminals due to its source code being leaked last year.
Users who fall for this attack are, no doubt, simply wanting to do the right thing. And it’s this inability to distinguish helpful from harmful that demands users be enrolled in continual Security Awareness Training so they can better understand how to identify suspicious or malicious emails immediately upon receiving them.
 Here's how it works:
Here's how it works:




