 New Ransomware CrypVault Evades AV With Simple Batch Scripts
New Ransomware CrypVault Evades AV With Simple Batch Scripts
A new ransomware strain dubbed CRYPVAULT by Trend Micro is being spread as an email attachment. It's currently focusing on Eastern Europe and is making its way to Europe and America.
It's a novel approach. In an attempt to bypass any and all endpoint protection, the user is social engineered to open an attached Javascript file. The phishing attack does not have an executable as a payload. Next, it uses the command box to run a batch file that encrypts the files.
According to a Monday post by Michael Marcos, threat response engineer with Trend Micro, CRYPVAULT encrypts the files and then makes them appear to the end-user as if they were quarantined, by giving them the .vault extension. Here is the schematic of the infection chain, courtesy Trend Micro:
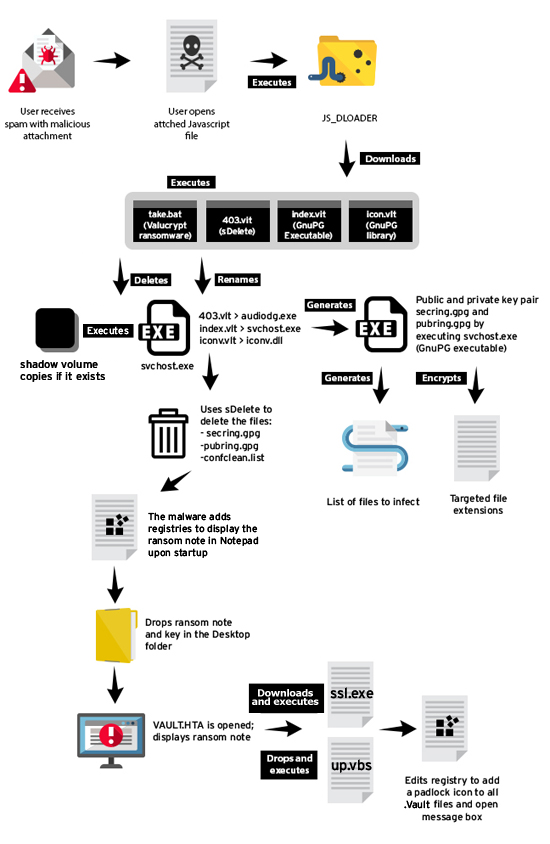
Adam Greenberg at SCMagazine said: “The act of disguising the users' encrypted files as quarantined files possibly aims to raise urgency for users to take action on their files,” Marcos told SCMagazine.com in a Monday email correspondence, going on to add, “Appending a .vault file extension can also be used as a marker for the malware to know that the file is already encrypted.”
When executed, CRYPVAULT installs an open source encryption tool, GNU Privacy Guard (GnuPG), which generates an RSA-1024 public and private key pair that encrypts files with numerous extensions, including .doc, .pdf, .rtf, .jpg, and .zip, the post indicates. The ransomware then appends the .vault file extension to encrypted files.
Upon attempting to open an encrypted and locked file, a prompt appears that instructs victims on how to go about paying the ransom, according to the post. Additionally, a text file downloaded by the malware provides instructions, and the attached file name, ransom note and ransomware support portal are in the Russian language.
To ensure victims cannot unlock their files without paying the ransom, CRYPVAULT uses a Microsoft tool known as SDelete to delete key files used in the encryption process, including ‘secring.gpg,' ‘vaultkey.vlt,' and ‘confclean.lst,' Marcos wrote in the post, adding that the ransomware uses 16 overwrite passes.
“This means that the malware makes sure that the decryption key is irrecoverable on the affected system by data recovery tools,” Marcos said.
Additionally, CRYPVAULT downloads and executes the Browser Password Dump hacking tool, which extracts stored login passwords from various browsers, including Firefox, Internet Explorer, Chrome, Safari and Opera, the post notes.
Particularly interesting for Marcos is that CRYPVAULT is not coded using a programming language such as C++, C# or .NET, he said.
“The ransomware is written in a batch script (the script is executed line per line in the command line/MS-Prompt),” Marcos said. “It did not import any libraries or can create functions. The commands were executed from top to bottom.”
He added, “The ransomware is purely written in scripts – JavaScript for the downloader and batch script for the ransomware. The components that come with the malware do the bulk of the malicious routines. This shows how easy one can make a ransomware. Other crypto-ransomware variants coded their encryption routines.”
Marcos suggested not paying the ransom because there is no guarantee that the correct keys will be provided – instead, he said the best option is to rebuild from a recent backup.
The malware was analyzed and discussed last month on BleepingComputer.com, where the ransomware was referred to as VaultCrypt and was said to be making its way to English speaking regions."
It is clear that more and more Eastern European cyber mafias are jumping on the ransomware bandwagon, and that employees need to be trained thoroughly not to fall for these types of social engineering attacks.
Find out how affordable security awareness training can be today!





