Larry Abrams, who runs Bleepingcomputer was first to report on a new strain of ransomware called RAA. The criminal coders took the somewhat unusual step of writing the whole thing in JavaScript making it more damaging in certain situations, and also install the Pony password stealer for good measure.
Larry wrote that it is being distributed by email through attachments that pretend to be a regular Doc file. Since JavaScript itself does not have crypto functions, the bad guys use the CryptoJS library which allows them to use AES encryption to lock up their victims' files. Here is how the fake attachment looks:
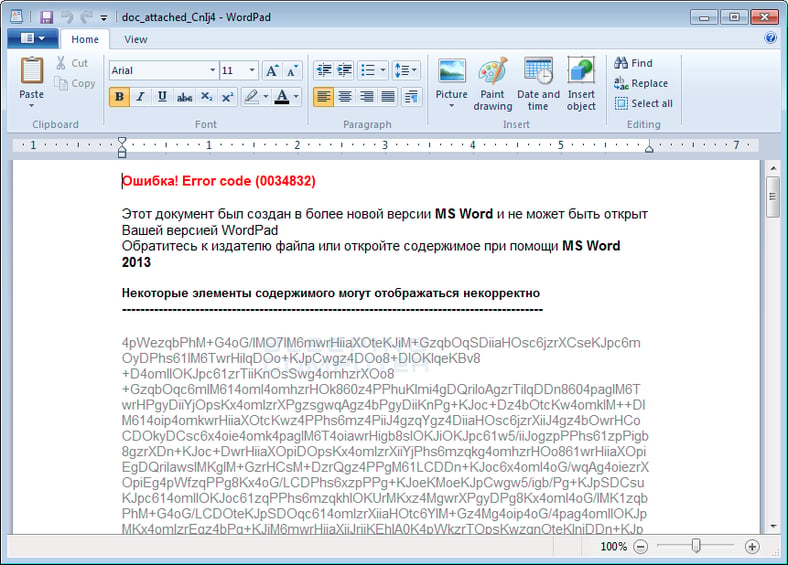
Opening the attachment does not visibly do anything, but appears to the victim as a corrupted file. However, back at the ranch it is busy as a beaver doing its dirty work in the background, including deleting the Windows Volume Shadow Copy so the encrypted files cannot be recovered.
The RAA strain is set to be persistent so that the ransomware runs every time Windows is rebooted and even encrypts any new files created since the most recent login. Ransom32 is another strain developed in JavaScript, however RAA is different in that it is a standard JS file and not delivered via an executable.
Disabling the Windows Script Host will stop a JS file from executing outside of the browser, Javascript will still function within a web browser. See the full technical detail over at Larry's post.
Ransomware Hostage Rescue Manual
Get the most complete Ransomware Manual packed with actionable info that you need to have to prevent infections, and what to do when you are hit with ransomware.





