Researchers at Security firm SentinelOne reported that a group of hackers is using malicious PowerPoint files to distribute 'Zusy,' a banking Trojan, also known as 'Tinba' (Tiny Banker).
They said in a blog post: "A new variant of a malware called 'Zusy' has been found in the wild spreading as a PowerPoint file attached to spam emails with titles like 'Purchase Order #130527' and 'Confirmation.' It's interesting because it doesn't require the user to enable macros to execute. Most Office malware relies on users activating macros to download some executable payload which does most of the malicious stuff, but this malware uses the external program feature instead."
This new social engineering attack doesn't trick users to enable macros; instead it executes malware on a targeted system using PowerShell commands embedded inside the PPT file, and does not rely on Javascript or VBA for the execution method either.
Best yet, the malicious PowerShell code hidden inside the document triggers as soon as the victim moves/hovers a mouse over a link, which downloads an additional payload on the compromised machine -- even without clicking it.
However, it's not all that bad, the code doesn’t execute automatically as soon as the file is opened. Instead, both Office 2013 and Office 2010 display a severe warning by default:
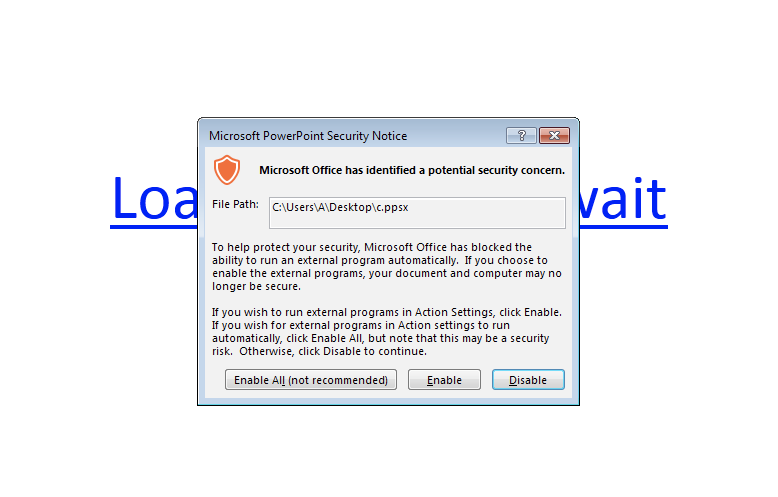
Users might still somehow enable external programs because they have not been stepped through new-school security awareness training. Also, some configurations may possibly be more permissive in executing external programs than they are with macros.
The researchers said the attack doesn't work if the infected file is opened in the PowerPoint Viewer, which simply refuses to execute the program. But this vector could still work in cases where end-users are getting successfully social engineered.
Your Employees Are Your Last Line Of Defense
Bad guys go for the low-hanging fruit. If you want to spend less time putting out fires, get more time to be proactive, and get the things done you know need to be done, step employees through effective security awareness training.
It will help you prevent CEO fraud or ransomware infections or at least make it very hard for the bad guys to social engineer employees. Find out how affordable this is for your organization:
PS, don't like to click on redirected buttons? Cut & paste this link in your browser:
https://info.knowbe4.com/kmsat_get_a_quote_now





