 A recent suspicious phone call was brought to our attention. It looks to be the beginning of a phishing campaign and demonstrates the lengths cybercriminals will go to in order to ensure success.
A recent suspicious phone call was brought to our attention. It looks to be the beginning of a phishing campaign and demonstrates the lengths cybercriminals will go to in order to ensure success.
One of our threat analysts reached out to me today and shared an email they received from a customer who wanted to bring to our attention a vishing call he had taken that felt far more like social engineering than it did a legitimate call.
Take a read:
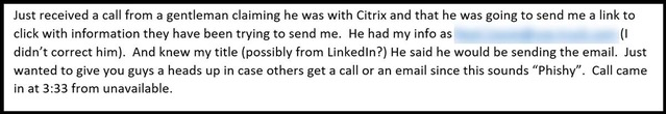
Now, it’s completely possible that this was a business development rep from Ctirix. But, from the tone conveyed and the inferred bit about the email being incorrect, it doesn’t sound like they ever got anything legitimate from Citrix.
Assuming this to be a vishing email designed to bring the victim’s defenses down when they are sent a phishing email, it means there was some diligence done using online tools like LinkedIn and other business contact data mining services to pull together a profile of the potential victim before calling. They, then identified a brand and to impersonate and “story” to use that would yield the highest engagement rate.
The idea of vishing before phishing isn’t out of the realm of possibility; the use of social engineering takes all forms. And a layered attack strategy likely has a better chance of succeeding than simply sending, in this case, an unsolicited email from a known vendor, which - in the case of IT pros specifically – would probably have a very low success rate.
Educate your users with Security Awareness Training about attacks like this, along with the use of vishing, phishing and social engineering as separate tactics. Attacks are getting more sophisticated to increase their chances of success. Without training, you users may fall more easily for these types of attacks.
 Here's how it works:
Here's how it works:




