 Yes – you read that right: Cybercriminals have found a way to use 1830’s technology to trick 2020s security solutions into not identifying phishing attachments as malicious.
Yes – you read that right: Cybercriminals have found a way to use 1830’s technology to trick 2020s security solutions into not identifying phishing attachments as malicious.
Like you, when I first read about this I shook my head and through “no way – how would that even work??!?” But according to a post on reddit, the bad guys realized they could digitally encode their malicious java script in Morse Code, effectively bypassing any email scanners.
The phishing attack starts out like any other, using some basic social engineering around paying an invoice and hosting an attachment made to look like an invoice with the filename '[company_name]_invoice_[number]._xlsx.hTML.'
But upon further inspection of the attachment, it leverages javascript, containing a basic decoding function where each letter and number is assigned a Morse code value, and then calls to decode a massive amount of Morse code stored within the file.
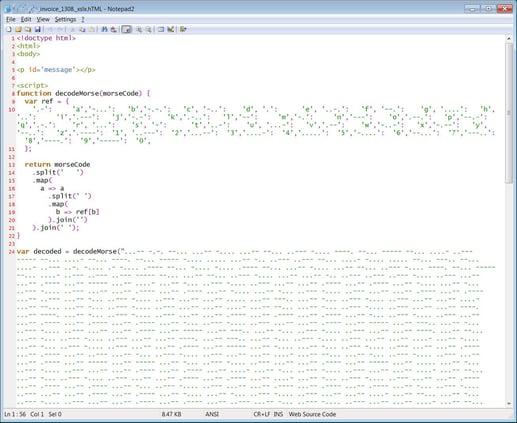
Source: Bleeping Computer
The result is when the html attachment is scanned, its contents appear benign to a security solution. But when run, the script converts the Morse code into two additional javascript tags that are injected into the page and executed.
The result of all this is a pretty creative rendering of a fake Excel document and an Office 365 logon screen, stating the user’s session had timed out.
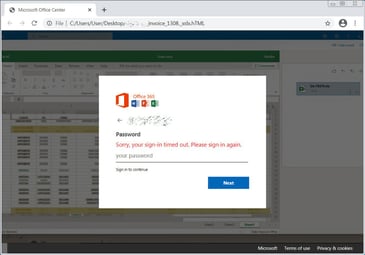 Source: Bleeping Computer
Source: Bleeping Computer
Creative? Yes. Unique? No – bad guys can derive even their own simple character replacement encoding (e.g., ‘A’ would be replaced with ‘D’, ‘B’ with ‘E’, etc.) and one can achieve the same result.
The real stopping point here is the bogus email theming and horrible attachment name. Users that undergo Security Awareness Training are positioned to quickly see this for what it is and stop the attack before it goes any further than making it to the Inbox.
 Here's how it works:
Here's how it works:




