 The use of open redirects from legitimate domains makes phishing emails that much more believable and credible, obfuscating the dangerous nature of these attacks.
The use of open redirects from legitimate domains makes phishing emails that much more believable and credible, obfuscating the dangerous nature of these attacks.
In the ongoing saga of attacks on Microsoft 365 users, security analysts at Microsoft recently announced a widespread attack that utilizes open redirects – a technique used in web development to point to the URL visitors of a website should be taken to once the initially-visited page is done processing the visit.
A simple example of an open redirect is the following:
https://example.com/redirect.php?url=http://attacker.com
According to Microsoft, attackers will use a bit more trickery to fool those that choose to hover over links in emails before clicking on them, embedding a malicious URL within what appears to be a trusted URL (note the red portion of the URL below):
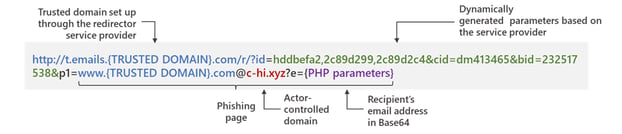
Source: Microsoft
In many cases, redirects to malicious URLs first take visitors to Google reCAPTCHA pages to further obfuscate the nature of the final destination from security solutions designed to evaluate email links.
While evaluating destination URLs via hovering over links in an email is definitely a good security practice, threat actors are becoming wise to this and are taking steps such as those mentioned above to make it even more difficult to spot a malicious link.
Users should be taught via Security Awareness Training to be more mindful of the actual message being sent – if unsolicited, it should be treated with at least a bit of distrust and scrutiny, being certain it is legitimate before engaging with links – benign or malicious.
 Here's how it works:
Here's how it works:




