
Cybersecurity researchers have developed a new keystroke impersonation attack that avoids being detected by keystroke-based biometric security solutions.
The idea of using biometrics for security purposes has been around for years. The idea of using a thumbprint, a retina scan, or your voice have been made part of very secure environments. But the idea of giving up something that so-uniquely identifies a person has made some users hesitant.
The idea of using keystrokes – which seems far less intrusive than, say, scanning you eye – has been around for many years as well. Some security products use keystroke characteristics to confidently identify an individual.
The latest research entitled “Malboard: A Novel User Keystroke Impersonation Attack and Trusted Detection Framework Based on Side-Channel Analysis” discusses a new attack that generates and sends malicious keystrokes that mimic the victim user's behavioral characteristics. So, solutions identifying users based on keystroke can be fooled into believing it’s the actual user making requests to access and exfiltrate sensitive data.
The introduction of such malware indicates that a) it’s possible to easily mimic a user, further confounding the detection of external attacks that are leveraging compromised internal credentials and, b) the bad guys will begin to incorporate this kind of capability into their automated attacks as security vendors look to further their ability to identify that the user making a request is actually the requesting user.
The Malboard attack method is just the latest innovative attack method. But, to be effective, the code behind Malboard needs to somehow be present on an endpoint. That means traditional delivery mechanisms such as phishing attacks using malware delivery would be necessary. Users undergoing Security Awareness Training are best-equipped to spot malicious email and web content, lowering the chance of successful attack.
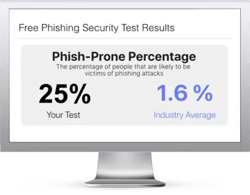
Free Phishing Security Test
Find out what percentage of your employees are Phish-prone™
Would your users fall for convincing phishing attacks? Take the first step now and find out before the bad guys do. Plus, see how you stack up against your peers with phishing Industry Benchmarks. The Phish-prone percentage is usually higher than you expect and is great ammo to get budget.
 Here's how it works:
Here's how it works:
- Immediately start your test for up to 100 users (no need to talk to anyone)
- Customize the phishing test template based on your environment
- Choose the landing page your users see after they click
- Show users which red flags they missed, or a 404 page
- Get a PDF emailed to you in 24 hours with your Phish-prone % and charts to share with management
- See how your organization compares to others in your industry
PS: Don't like to click on redirected buttons? Cut & Paste this link in your browser:
https://www.knowbe4.com/phishing-security-test-offer





