 Maktub Locker is the name of a new Russian strain of ransomware. The word Maktub is Arabic for "fate", suggesting it is inevitable you will get infected with ransomware. They have spent a lot of time on the website and the code was put together by professionals with extensive experience in writing malicious code. If these guys don't make it in the ransomware racket, they can start a second career in web design. This whole thing is well-polished start to finish.
Maktub Locker is the name of a new Russian strain of ransomware. The word Maktub is Arabic for "fate", suggesting it is inevitable you will get infected with ransomware. They have spent a lot of time on the website and the code was put together by professionals with extensive experience in writing malicious code. If these guys don't make it in the ransomware racket, they can start a second career in web design. This whole thing is well-polished start to finish.
At the moment, the strain is spread via email with a .scr attachment that pretends to be a document with a Terms-Of-Service update. The social engineering tricks are also professional grade. When the user opens the document, it really displays a fake TOS update in .rtf format. However, in the background, their files are being encrypted. Our friends at Bleepingcomputer and Malwarebytes have had a look and here are some highlights.
Both Encrypts And Compresses
Maktub Locker does not need to download a key from a Command and Control server – the data can be encrypted offline. The new and surprising thing is that encrypted files are much smaller than the original ones. It seems this ransomware not only encrypts but also compresses files. What an unexpected benefit!
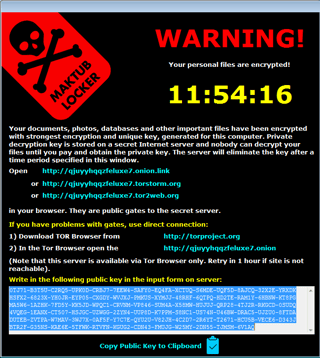
Well Designed Payment Website For Victims
Today, it's pretty standard to provide a TOR-based website for payments. Maktub is no different, and comes with a "cold- comfort-demo" allowing the decryption of 2 selected files to show they can give you your files back. Both the ransom note and the website are in English. Here is how it looks, very polite indeed:

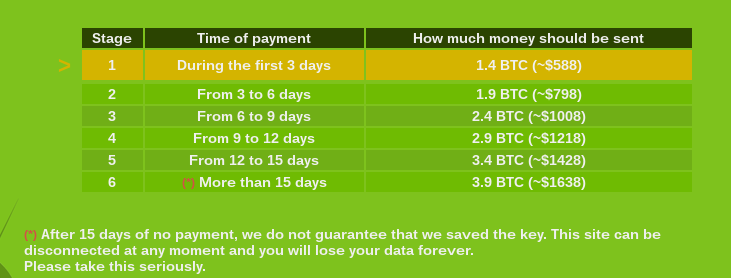
Ransom from 1.4 bitcoin to a max of 3.9 bitcoins
Maktub Locker is designed following the "criminal industry standard" that encrypts your data and then ransoms your files for a low amount to start with, in this case 1.4 bitcoins. After a certain amount of time, you enter a new stage where the ransom amount increases, and Maktub ultimately the ransom price tops out at 3.9 bitcoins. Here is their schedule:
What To Do About It
Suddenly, the low cost for effective security awareness training comes into perspective as a great way to manage the ongoing problem of social engineering. Find out how affordable that is here.
And here are some excellent suggestions from Steve Ragan at CSO:
- Avoid mapping your drives and hide your network shares. WNetOpenEnum() will not enumerate hidden shares. This is as simple as appending a $ to your share name.
- Work from the principle of least permission. Very few organizations need a share whereby the Everyone group has Full Control. Delegate write access only where it’s needed, don’t allow them to change ownership of files unless it’s a must.
- Be vigilant and aggressive in blocking file extensions via email. If you’re not blocking .js, .wsf, or scanning the contents of .zip files, you’re not done. Consider screening ZIP files outright. Consider if you can abolish .doc and .rtf in favor of .docx which cannot contain macros.
- Install the old CryptoLocker Software Restriction Policies which will block some rootkit-based malware from working effectively. You can create a similar rule for %LocalAppData%\*.exe and %LocalAppData%\*\*.exe as well. It was pointed out in the Reddit comments, that if it’s at all feasible, run on a whitelist approach instead of a blacklist. It’s more time-intensive but much safer.
- Backups. Having good, working, versionable, cold-store, tested backups makes this whole thing a minor irritation rather than a catastrophe. Even Windows Server Backup on a Wal-Mart External USB drive is better than nothing. Crashplan does unlimited versioned backups with unlimited retention at a flat rate, and there’s a Linux agent as well. Hell, Dropbox does versioned backups. Get something.
Get the most informative and complete hostage rescue manual on Ransomware.
This 20-page manual (PDF) is packed with actionable info that you need to prevent infections, and what to do when you are hit with malware like this. You also get a Ransomware Attack Response Checklist and Prevention Checklist.
Related Pages: Ransomware





