 Graham Cluley was the first to report on a new Locky ransomware phishing attack where the emails claim to be "credit card suspended" and "suspicious money movement" warnings.
Graham Cluley was the first to report on a new Locky ransomware phishing attack where the emails claim to be "credit card suspended" and "suspicious money movement" warnings.
He said: "In the last few days there have been a spate of spammed-out attacks using similar techniques to dupe unwary internet users into clicking on an attachment that will lead to their Windows PC being infected with the notorious Locky ransomware."
This attack is now using threats claiming that there have been “suspicious movements” of funds out of your bank account and/or that your credit card account has been suspended. Here is an example of the suspicious money movement social engineering tactic:
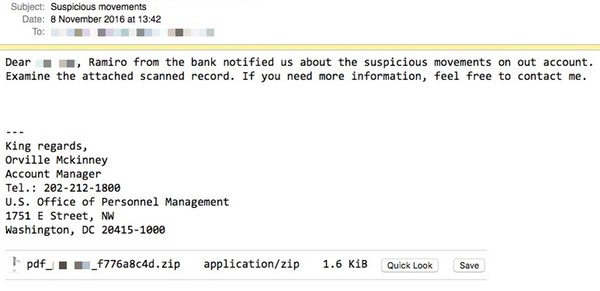
Attached to the email is a ZIP file containing a malicious Javascript file (.JS), that if the employee opens it, downloads the most recent version of the Locky ransomware from a remote server from one of five different URLs.
Next, the ransomware is executed without any further user interaction. Some anti-virus products detect the malicious Javascript as Trojan.JS.Downloader.GXW, but that changes on a regular basis. Here is an example of the credit card suspension email:
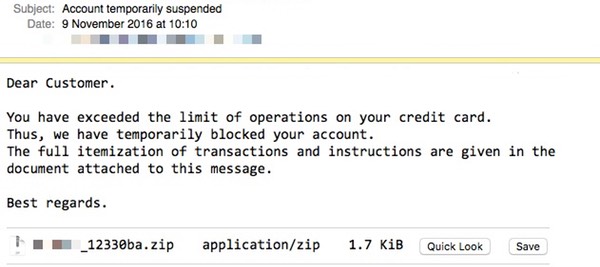
The Locky cybercriminals are well-organized and highly automated. They change the names and contact details used in these phishing emails so you cannot rely on them being the same. Ransomware is cybercrime's most successful business model, so count on these attacks increasing in the future.
Have your defense-in-depth fully in place, have weapons-grade backups, and step your users through new-school security awareness training which includes frequent simulated phishing attacks to keep them on their toes with security top of mind.
11/11/2016 - Correcctions and Amplifications Department: Turns out that Phishme reported on this even earlier, (November 8th, 2016) and pointed out that the address was the Office of Personnel Management where 22 million government workers profiles had been exfiltrated.
Free Ransomware Simulator Tool
How vulnerable is your network against ransomware attacks?
Bad guys are constantly coming out with new versions of ransomware strains to evade detection. Is your network effective in blocking ransomware when employees fall for social engineering attacks?
KnowBe4’s Ransomware Simulator "RanSim" gives you a quick look at the effectiveness of your existing network protection. RanSim will simulate 10 ransomware infection scenarios and show you if a workstation is vulnerable to infection.





