 At a time when tensions are high with questionable election results, lawsuits, and an apparent “president-elect”, makers of Qbot are taking full advantage of the opportunity.
At a time when tensions are high with questionable election results, lawsuits, and an apparent “president-elect”, makers of Qbot are taking full advantage of the opportunity.
Qbot is one of the nastiest trojans around. I’ve written about it stealing all kinds of information and hijacking email threads as part of targeted attacks. A new report from the security researchers at Malwarebytes highlights a new campaign targeted the emotions of those caught up in the presidential election using email messages and accompanying attachments sent under the guise of information regarding election interference.
No one wants “their” candidate to not be elected, so this is a perfect way to take advantage of already heightened emotions. And with the electors not due to finalize the vote until December 14th, this phishing campaign is still very relevant.
The good news is, according to Malwarebytes, the attack requires the user to perform a few steps. Emails are sent with a ZIP attachment that must be opened. Once extracted, an Excel spreadsheet needs to be opened. And once opened, the user must following the bogus “DocuSIgn” directions and enable macros using the “Enable Content” feature within Excel.
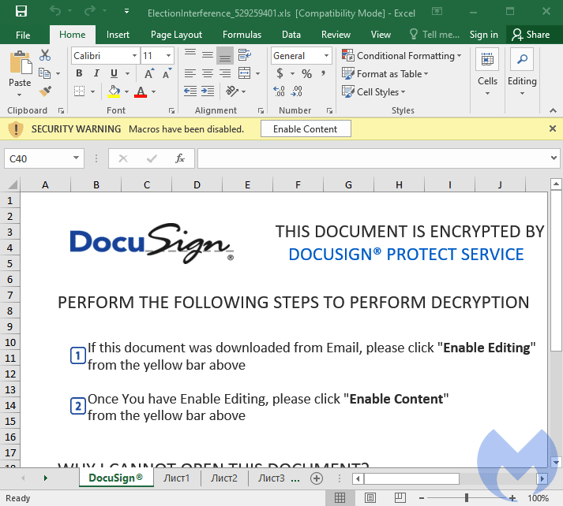
Users that have undergone Security Awareness Training can spot this attack as such a mile away. The oddity found in sending a zipped document about election fraud alone is cause for suspicion.
You don’t want to mess with a phishing attack that involves Qbot, and the best defense is one that involves your users.
 Here's how it works:
Here's how it works:




