This Site Creates Robocalls to Steal People’s Credit Card PINs
A June 30, 2017 post on Motherboard revealed a V1.0 of a site that does automated social engineering as a service, and has been in operation since June 2016.
They wrote: "In the internet underground, cybercriminals regularly exchange stolen credit card and debit card numbers and people's personal information—data they usually refer to as "dumps." But having someone's credit card number isn't great if you just want to get some cash. For that you'd need their ATM pin too.
That's where a relatively new dark web service comes in. It claims to offer a simple, automated way to trick targets into giving up their PINs or other data such as mother's maiden name. With this information, malicious hackers could access the target's online banking accounts or other sensitive accounts."
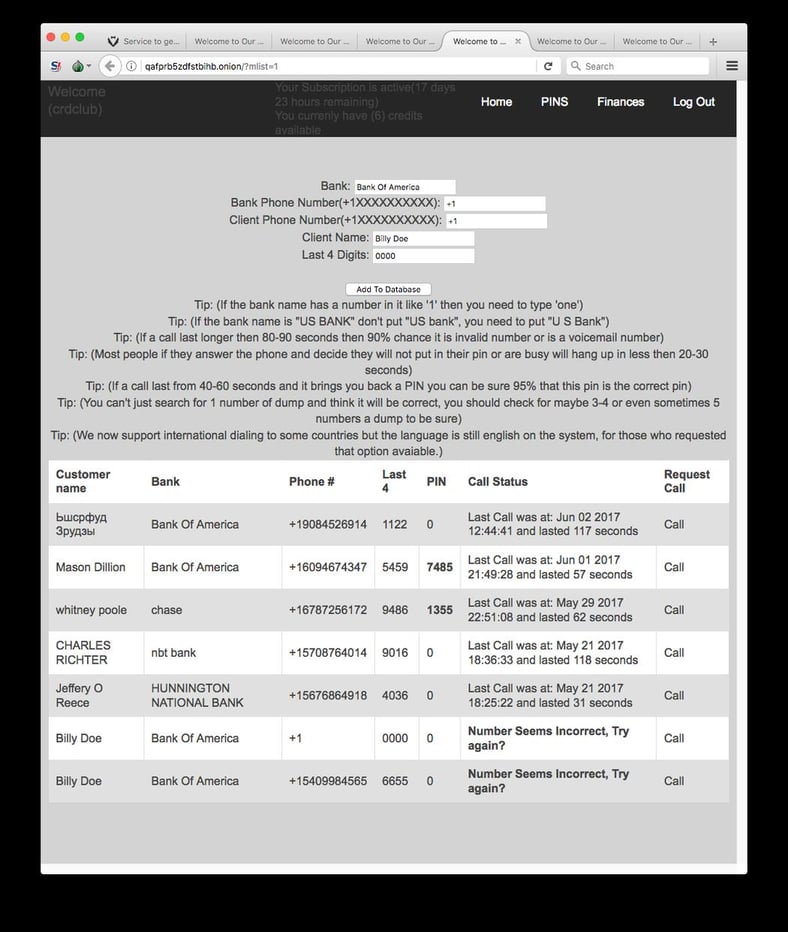
How this Social Engineering As A Service Works
The criminal customer becomes a subscriber to the site and pays a monthly fee of about $250. Next, they upload the data of the person they want to attack (their name, phone and their bank) and the service creates a robocall to social engineer the victim out of their pin. It's a real example of automated social engineering as a service.
"The system is simple," the website, which doesn't have a specific name, states. "The system will ask them to confirm their atm pin number. If the victim puts in their pin number you will see it in your panel. After that you just go cash out."
"While the service seems a little rough around the edges—and it might just be an elaborate scam—it's definitely innovative, according to security firms and researchers that monitor the dark web.
For Andrei Barysevich, a researcher at security firm Recorded Future, "the service seems to be ingeniously clever."
"We've not seen this level of automation paired with a phone social engineering service before," Mark Arena, the CEO of dark web monitoring firm Intel 471, told Motherboard in an online chat.
Researchers from Digital Shadows, another company that scours the dark web, traced the origins of the site back to July of 2016, when a hacker named goldrose advertised it on the popular dark web cybercrime bazaar AlphaBay. Since then, goldrose has advertised the site on other cybercrime sites where people exchange stolen credit card numbers, also known as "carding" forums."
Full article at Motherboard
Sites Like These Are Why We Are Working On AIDA
AIDA stands for Artificial Intelligence Driven Agent and uses artificial intelligence to dynamically create integrated campaigns that send emails, text and voicemail to an employee, simulating a multi-vector social engineering attack. It attempts to have the employee either click on a phishing link, tap on a link in a text message, or respond to a voice mail – any of which could compromise your network. In short, AIDA uses Artificial Intelligence to inoculate your employees against social engineering.
See it for yourself and get a live, one-on-one demo.

PS: Don't like to click on redirected buttons? Cut & Paste this link in your browser:
https://info.knowbe4.com/kmsat-request-a-demo




