 Cybercriminals intent on using a mobile device as a second factor of authentication are now using texts and very realistic-looking mobile sites to steal details needed to perform SIM swaps.
Cybercriminals intent on using a mobile device as a second factor of authentication are now using texts and very realistic-looking mobile sites to steal details needed to perform SIM swaps.
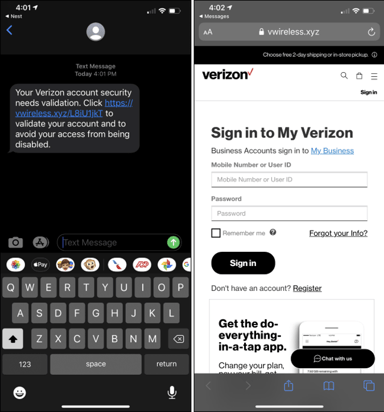
Source: How To Geek
Should the victim walk through the entire scam, they give up every bit of information needed to take control of their account. It stands to reason the next step is a SIM swap, but that’s only worthwhile when used as part of a spear phishing scam intent on stealing the very same user’s online credentials to, say, their Office 365 account or banking site.
This scam highlights how an attack that simply uses a) a trusted device and b) a realistic-looking website can fool an unsuspecting user. The only real telltale sign in this scam is the URL (see the image above). You organization’s only real defense against this portion of what can only be assumed is a larger attack is to elevate the user’s security mindset and vigilance when receiving texts, opening emails, and surfing the web. Security Awareness Training continually keeps users up-to-date on the latest attack methods and the need for user participation in organizational security.
The illusion of legitimacy this attack leverages is a real benefit to cybercriminals; with it, they can fool just about anyone if the context and timing is right. Teaching users to always have their defenses up is, legitimately, your only viable defense.
 Here's how it works:
Here's how it works:




