 A new version of the Cerber ransomware family has adopted new techniques to make itself harder to detect by endpoint security software that uses machine learning for detection. It is now using a new loader designed to hollow out a normal process where the code of Cerber is run instead.
A new version of the Cerber ransomware family has adopted new techniques to make itself harder to detect by endpoint security software that uses machine learning for detection. It is now using a new loader designed to hollow out a normal process where the code of Cerber is run instead.
Cerber reared its ugly head March last year and has rapidly grabbed marketshare by furiously innovating and using different attack vectors and distributions channels. It spreads mostly through phishing emails, but also uses exploit kits.
In August 2016, Invincea researchers discovered that Cerber was being distributed by Betabot, which was designed as a banking information stealing Trojan but recycled for ransomware. Recently, Cyren researchers reported that Cerber is being dropped by Kovter, a click-fraud Trojan which was dropping Locky several months ago.
Trend Micro reports that the new loader was necessary because machine learning security code detect malicious files based on features instead of signatures. The new packaging and loading mechanism employed by Cerber can cause problems for static machine learning approaches–i.e, methods that analyze a file without any execution or emulation. In other words, the way Cerber is packaged could be said to be designed to evade machine learning file detection. For every new malware detection technique, an equivalent evasion technique is created out of necessity.
The good news, the researchers say, is that this new evasion technique can be defeated by security approaches that employ multiple layers of protection, because the attack has other weaknesses, such as the use of an unpacked .DLL file. Solutions that don’t overly rely on machine learning can still prove effective against this threat.
And of course you want to step all your end-users through new-school security awareness training, so that they spot the phishing emails when they make it through all the filters.
We're excited to announce a new resource for you, our new Ransomware Simulator.
How vulnerable is your network against ransomware? Bad guys are constantly coming out with new versions of ransomware strains to evade detection. Is your network effective in blocking ransomware when employees fall for social engineering attacks KnowBe4’s Ransomware Simulator "RanSim" gives you a quick look at the effectiveness of your existing network protection. RanSim will simulate 10 ransomware infection scenarios and show you if a workstation is vulnerable to infection.
Here's how RanSim works:
![]() 100% harmless simulation of a real ransomware infection
100% harmless simulation of a real ransomware infection![]() Does not use any of your own files
Does not use any of your own files![]() Tests 10 types of infection scenarios
Tests 10 types of infection scenarios![]() Just download the install and run it
Just download the install and run it ![]() Results in a few minutes!
Results in a few minutes!
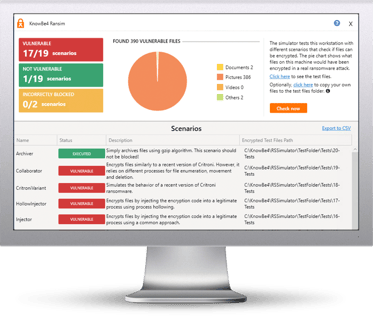
NOTE: Created for Windows-based workstations running Windows 7+. RanSim does not alter any existing files on disk. As part of the simulation RanSim does enumerate all files on the local disk(s). For the purposes of encryption, simulated data files are downloaded from the Internet.
Don't like to click on redirected buttons? Copy & paste this link in your browser:
https://www.knowbe4.com/ransomware-simulator





