 In an interesting twist, cybercriminals utilize a well-known technology to keep security solutions from identifying a “failed payment” email as being fraudulent.
In an interesting twist, cybercriminals utilize a well-known technology to keep security solutions from identifying a “failed payment” email as being fraudulent.
We’ve all sat there frustrated, being asked to “click on all the boxes that contain” traffic lights, cars, bicycles, or to type in strangely-presented words – all in the name of proving we’re human. CAPTCHA is used by countless websites today as a means of keeping bots out and allowing humans to proceed on a website.
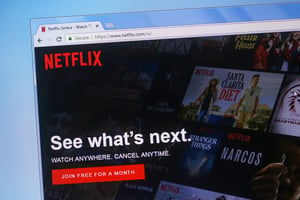
But a recent phishing attack was spotted and analyzed by security researchers at Armorblox, purporting to be from Netflix customer support with a payment issue, was found to use a CAPTCHA landing page before taking the potential victim to a spoofed Netflix logon page.

This credential scam is elegant and, dare I say, brilliant. What better tool to keep a computer from detecting if the scam’s landing page is legitimate or not than a technology designed to keep computer systems out?
In addition to keeping automated security systems from spotting the fake Netflix logon page, the use of the well-known CAPTCHA adds a layer of familiarity for potential victims, likely making them more prone to continuing through the remainder of the scam.
While organizations usually aren’t concerned about their employee’s Netflix credentials, this same method can just as easily be used to obfuscate spoofed pages designed to steal online business credentials. Educating users with Security Awareness Training on evolving tactics, such as the use of CAPTCHA, can help elevate the employee’s ability to spot a scam and avoid falling for really brilliant tactics, like the ones used in this attack.
 Here's how it works:
Here's how it works:




