A research team from Google collaborated with the cybersecurity experts from the University of California, Berkeley to scrutinize the activities of these online miscreants. After about 1 year of research, they have now finally come out with the results which put light on one major fact that most of these passwords are obtained by the hackers in two ways.
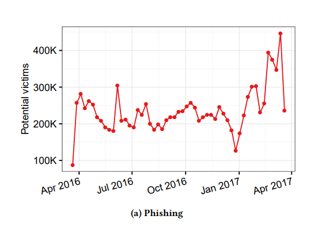
Email phishing, which has been enlisted as one of the major ways account for about 12 million credential thefts in the 2016-2017 period while the third-party breaches account for about 3.3 billion credential thefts of the users in the same time period.
Their conclusion:
"In this work we presented the first longitudinal measurement study of how miscreants obtain stolen credentials and subsequently bypass risk-based authentication schemes to hijack a victim’s account.
In total, we identified 788,000 potential victims of off-the-shelf keyloggers; 12.4 million potential victims of phishing kits; and 1.9 billion usernames and passwords exposed via data breaches and traded on blackmarket forums.
Through a combination of password re-use across thousands of online services and targeted collection, we estimated 7–25% of stolen passwords in our dataset would enable an attacker to log in to a victim’s Google account and thus take over their online identity due to transitive trust.
However, we showed how blocking login attempts that fail to match a user’s historical login behavior or device profile help mitigate the risk of data breaches and keyloggers, and to a lesser extent phishing.
We are now using these insights to improve our login defenses for all users. Our findings illustrate the global reach of the underground economy surrounding credential theft and the need to educate users about password managers and unphishable two-factor authentication as a potential solution."
Full PDF here.
 Here's how it works:
Here's how it works:




