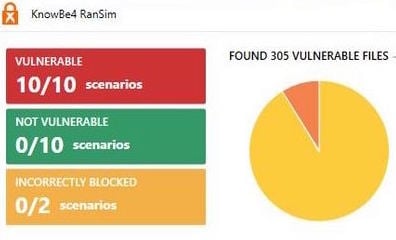
 So, you downloaded KnowBe4's Ransomware Simulator test and your antivirus security software failed one or more of the ransomware scenarios. When this happens we almost always get asked: "How do I fix this?".
So, you downloaded KnowBe4's Ransomware Simulator test and your antivirus security software failed one or more of the ransomware scenarios. When this happens we almost always get asked: "How do I fix this?".
First of all, you are not alone and other security tools are not catching this either. A recent survey of companies that suffered successful ransomware attacks during the last 12 months showed that antivirus wasn’t the only security solution that came up short. Victims reported that 95% of the attacks bypassed the victim’s firewall(s); 77% of the attacks bypassed email filtering; 52% of the attacks bypassed anti-malware; and 33% of the attacks were successful even though the victim had conducted security awareness training. (Must have been old-school, once-a-year training!)
So, how do I fix this?
1) First, check out this link which dives into the background of the RanSim that gives you some background what these scenarios are actually testing. Understand why the different tests show as vulnerable: Replacer, StrongCryptor, StrongCryptorFast, StrongCryptorNet, and WeakCryptor. The Test Scenarios section in the above link go into what happens with each scenario and how that particular scenario attempts to successfully run.
2) Make sure your defense-in-depth is fully in place.
- Take a look at your endpoint security, make sure you run the latest version of the software and the latest version of AV definitions.
- Make sure your patching discipline and backup procedures are weapons-grade quality.
- Reach out to your AV vendor and specifically ask about ransomware protection.
- Look at best-of-breed anti-ransomware solutions in the market to augment your end point security. Endpoint security software is the piece in the security puzzle that fails the RanSim test. Check out Virus Bulletin's latest RAP quadrant periodically to see how your vendor compares.
A good example is what happened in the Spiceworks forums, people reporting Sophos Endpoint security failing the RanSim tests. A rep from Sophos jumped in, saying: "Well... you need the InterceptX module in order to deal with ransomware (which is not part of the main end point security package)". People thought they were protected, yet they really weren’t. Here is a link to a Spiceworks post discussing various pass/fail situations, with the Sophos reps' comment: "RanSim"... A Ransomware Simulator ... - IT Security - Spiceworks. You'll see multiple posts with 0/5 vulnerabilities some with screenshots -- meaning their antivirus caught all the RanSim scenarios.
If you read the whole thread, the upshot is that having both a strong antivirus and good user awareness are critical keys in helping to prevent ransomware infections.
Knowbe4 does not recommend a specific security software solution, because ransomware frequently changes to evade detection so what works today might not work tomorrow. Our main recommendation of course is you are educating your employees. Build that human firewall and make sure they know what Social Engineering Red Flags™ to watch out for. By the way, this is a free PDF you can download and give all your users to pin on their wall.
New-school security awareness training is a must because even with filtering and end-point protection in place all it takes is a user enabling macros in an attachment and you've got ransomware spreading out into your network.
 This 26-page manual is packed with actionable info that you need to prevent infections, and what to do when you are hit with ransomware. You also get a Ransomware Attack Response Checklist and Prevention Checklist. You will learn more about:
This 26-page manual is packed with actionable info that you need to prevent infections, and what to do when you are hit with ransomware. You also get a Ransomware Attack Response Checklist and Prevention Checklist. You will learn more about:




