The latest from UK insurer Beazley‘s Breach Response Services division shows an increase in ransomware from attackers with little ability to decrypt ransomed data.
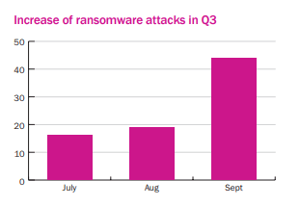
The nightmare starts with a computer screen being taken over with a message that the contents of the computer – and potentially more data within your network – has been encrypted. This is the increasing experience of more businesses today. According to Beazley’s October 2018 report, ransomware more than doubled in Q3 from August to September.
The ransomware nightmare normally ends in one of two ways: either you pay the ransom and the data is decrypted, or you recover the data from backup and ignore the attack entirely.
With 71% of ransomware incidents handled by Beazley in 2018 being SMBs, both means to end the nightmare have less than dependable results. According to cyber service vendor, Kivu Consulting, attackers are increasingly using bad strains of ransomware that corrupt data during encryption, or are unfamiliar with the decryption process enough to ensure organizational data is made right.
All this spells trouble for small businesses who are under-resourced, under-secured, and whos users aren’t savvy about cybersecurity.
So, what can SMBs do about Ransomware?
- Backup Everything Critical – From operational data, to computers you can’t live without; make sure you have backups in place regularly making copies of your network environment. Being able to restore is critical to the success of you getting through a ransomware attack unscathed.
- Protect Your Computers – Antivirus and/or Endpoint Protection software is important to keep ransomware from running on your systems in the first place.
- Educate Your Users – Enroll users in Security Awareness Training so they can spot phishing scams, social engineering tactics, and malicious links before clicking.
Ransomware isn’t going anywhere soon and, from the looks of the data from Beazley, SMBs need to begin doing something more to protect themselves.
Brand-New Ransomware Simulator Tool Now with Cryptomining Scenario
Bad guys are constantly coming out with new malware versions to evade detection. That’s why we’ve updated our Ransomware Simulated tool “RanSim” to include a new cryptomining scenario!
This new cryptomining scenario simulates a Monero cryptocurrency-mining operation on the local machine. Monero mining is the most popular cryptocurrency mined by real-world malware and takes a lot of CPU and GPU cycles to process the data necessary to generate the currencies.
Try KnowBe4’s NEW Ransomware Simulator tool and get a quick look at the effectiveness of your existing network protection against the latest threats.
RanSim will simulate 13 ransomware infection scenarios and 1 cryptomining infection scenario to show you if a workstation is vulnerable to infection.
Here's how RanSim works:
- 100% harmless simulation of real ransomware and cryptomining infection scenarios
- Does not use any of your own files
- Tests 14 different types of infection scenarios
- Just download the install and run it
- Results in a few minutes!
This is a complementary tool and will take you 5 minutes max. RanSim may give you some insights about your endpoint security you never expected!
Don't like to click on redirected buttons? Copy and paste this url into your browser:
https://info.knowbe4.com/ransomware-simulator-tool-1