 I have been in the cybersecurity business for 34 years. I am not an innately brilliant, but one of the things I seem to do well is to spot trends as they happen early in their cycle. It is likely just because I have seen so many trends and have been around for their growing development.
I have been in the cybersecurity business for 34 years. I am not an innately brilliant, but one of the things I seem to do well is to spot trends as they happen early in their cycle. It is likely just because I have seen so many trends and have been around for their growing development.
The growing trend I am seeing right now is increasingly targeted attacks. In the past, most malware and hacker attacks were almost accidental if your organization got hit.
The hacker(s) would send out 200M phishing emails and whoever was unlucky enough to open them and click on the links was almost random. I do not have any real figures, but I bet the number of attacks that targeted specific people and organizations numbered in the tens of thousands in a given year while the number of random attacks numbered in the trillions.
In the past, odds were that if your company got hit by a hacking attack or malware it was simply a matter of overwhelming odds. Sure, there have always been targeted attacks, but they were a miniscule percentage of the attacks in comparison.
That is changing. I can feel it. I can see it. And in an industry that does not need it, it has foreboding implications. Here is why and what it means.
Increased Nation-State Activity
After decades of worrying about cyber warfare by well-resourced nation-state adversaries, every worst-case scenario we worried about came to fruition throughout the last few years. You have Stuxnet taking down a nation’s nuclear infrastructure, doing damage that bombs could not do. You have a nation-state taking down an entire corporate conglomerate because they disagreed with a movie plot point. You have supply chain attacks compromising the nation’s best cybersecurity companies and every government department worth breaking into. You have nation-states using four zero-day attacks to break into the world’s most popular email servers with brazenness that assures you that the nation-state was not trying to be quiet about it.
We are in a period of intense nation-state activity and it is not likely to diminish anytime soon. If anything, based on history, it will likely only increase until the world comes together in a Kumbaya moment and stops this global madness. The increase in nation-state attacks means your organization is more likely to be targeted by them. It is just math. And nation-states love to use spear phishing where the targeted person or organization’s non-public details are used to make the phishing attack appear more legitimate.
If you want to learn more, see my one-hour webinar about nation-state attacks.
Increased Targeted Ransomware Attacks
The ransomware industry is maturing. The onesie-twosie ransomware gangs made up of a few people are being pushed out by a handful of major ransomware corporations. In everything but morality, they look like normal small or mid-sized organization with CEOs, HR, marketing, PR, developers, distribution, network infrastructure and tech support. They have feature set updates, competitive analysis, cross-selling opportunities and affiliates optimizing the Software as a Service (SaaS) subscription model envied by many legitimate organizations.
These ransomware corporations are increasingly targeting specific industries and companies. Why?
It takes them 80% of the same effort to infect and exploit a small or large company. Large companies pay more for nearly the same effort. They do not want to waste their time working to get a few thousand dollars when they can ask for hundreds of thousands to millions of dollars. The larger your company is, the more likely it is to be targeted. That did not used to be true. It is now. The ransomware groups are working smarter instead of harder.
Industry Familiarity
Malware gangs now target particular industries. Why? Maybe they got lucky the first few times in a particular industry, but now that they have studied them from the inside, read their emails and looked at their crown jewels, they understand how to best exploit that industry. Each industry has its own concerns, competitive assets and vernacular. Once those are known, it is far easier to craft spear phishing emails that seem more legitimate within that industry. Plus, when they break into a particular industry, they can use the compromised victim’s email accounts to send spear phishing emails to other trusted third parties. Our employees are told to be especially suspicious if an unexpected email arrives from someone they have never heard of or from a strange email address. But that same email is more likely to be opened and clicked on if it arrives from a long-time, trusted business partner, using a subject thread that has recently been used. Familiarity breeds success in the phishing world, too.
Compromised Insurance Company Lists
I have read a few times about cybersecurity insurance company networks being compromised by ransomware gangs so the criminals can learn about which customers are insured and for how much. The stolen customer lists are a virtual “Here is who to target next” invitation. I have even read of ransomware negotiators from the crimeware side correcting the victim’s negotiator on how much ransom the victim can afford to pay because they have seen the victim’s insurance policy details.
Note: Do not store your cybersecurity insurance policy on your network where it can be easily accessed by unauthorized intruders. Keep it offline or keep it especially encrypted where intruders cannot get to it.
Cybersecurity insurance companies often specialize in particular industries. Because the hackers are using the cybersecurity insurance companies as a jumping off point, this leads to the hackers concentrating on those industries as well.
For my entire career, I have seen survey after survey tell me what industries are seemingly being targeted by hackers and malware. What industries are targeted tends to change over time. What is different this time is that more companies within a specific industry are being targeted. The chances that your organization was compromised almost incidentally is growing smaller. These days, it is much more likely that your organization was targeted by a particular hacker group, for the reasons I listed above.
The effect of increased targeting is increasingly realistic spear phishing emails, either arriving from previously compromised, trusted business partners or emails which are simply more realistic for the industry being targeted. We are used to the generic, “pay this invoice”-type phishing emails that can apply to any targeted company. You will still see plenty of those. But train your employees to expect increasingly sophisticated and realistic spear phishing emails and increasing numbers of them.
Here are the three things I tell employees to look out for, which indicate something to be suspicious of:
- Email that was unexpected.
- Sender is asking the recipient to do something they have not done before for the sender.
- The action being requested could potentially be harmful to the recipient or their organization (e.g., provide confidential information, download something, click on a link, etc.)
If those three things are true, the recipient should verify the request another way, not using email (i.e., call them). This infographic shows several other red flags to watch out for in emails:
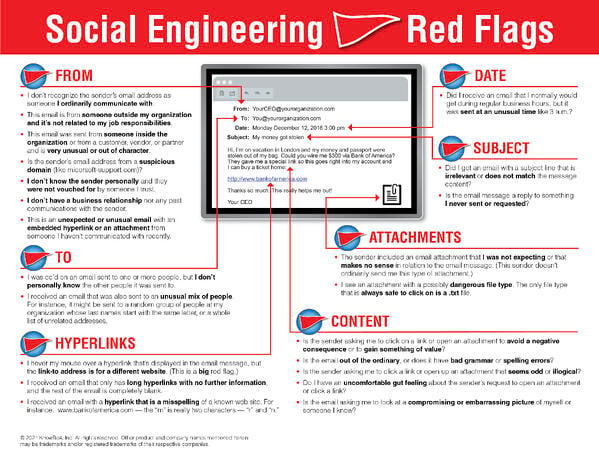 22 Social Engineering Red Flags PDF
22 Social Engineering Red Flags PDF
When you send simulated phishing emails to your organization’s employees, feel free to up the sophistication and “targetness” of the test attack. Do not let the real phishers be the only ones who are testing if your co-workers can spot a spear phishing attack.
 Here's how it works:
Here's how it works:




