.jpg?width=300&name=iStock-1199291222%20(2).jpg) The third quarter saw massive increases in activity by ransomware gangs both creating leak sites and posting to them about recent attacks on orgs that, presumably, didn’t pay the ransom.
The third quarter saw massive increases in activity by ransomware gangs both creating leak sites and posting to them about recent attacks on orgs that, presumably, didn’t pay the ransom.
We’ve seen more and more interest in ransomware attacks turning into ransomware-turned-data-breach attacks and the use of the extortion of going public with the data breach as a means to further influence the victim organization to pay the ransom.
Security vendor Digital Shadows’ Quarterly Update: Ransomware Trends In Q3 highlights their findings as ransomware groups adopt similar tactics:
- Maze, DoppelPaymer, and Sodinokibi made up 80% of alerts of the leak sites
- Conti and NetWalker ransomware groups joined the ranks of those hosting a leak site
- The number of leak sites by well-known ransomware groups rose to 7 by the end of Q3
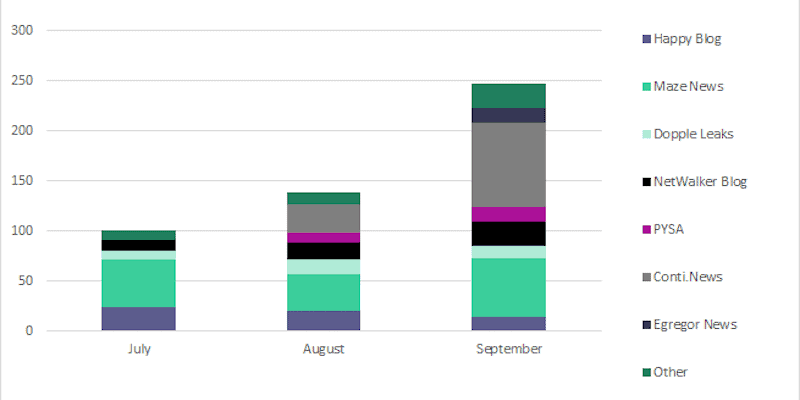
All this is bad news for organizations that aren’t truly prepared for Ransomware. It’s no longer a game of having backups, but being prepared for both a full-on data breach and a completely inoperable network. And with Ransomware-as-a-Service continuing to see growth, utilizing the same advanced attack methods and techniques as the leading ransomware variants, we’re going to need to buckle in for Q4 and into 2021.
Organizations can prepare for ransomware attacks using Security Awareness Training to educate their users on phishing attacks (the number one initial attack vector for ransomware) including how to identify them as malicious, and what to do should they think they receive one. Stopping phishing attacks before engaging with malicious content in email is the most effective way to reduce your threat surface and likelihood of successful attack.
 Here's how it works:
Here's how it works:




