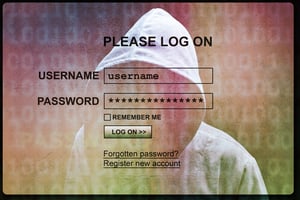
 Criminals are abusing SurveyMonkey to host redirect links to an Office 365 phishing page, researchers at Abnormal Security have found. The emails contain links to a real SurveyMonkey page, but clicking the links will take the user to a spoofed Microsoft login page that asks them to enter their Office 365 email address and password.
Criminals are abusing SurveyMonkey to host redirect links to an Office 365 phishing page, researchers at Abnormal Security have found. The emails contain links to a real SurveyMonkey page, but clicking the links will take the user to a spoofed Microsoft login page that asks them to enter their Office 365 email address and password.
“By using these legitimate services, attackers can bypass email URL detection systems deployed by many email security tools,” Abnormal Security says.
The attack is designed to fool humans as well, since the victim is clicking on what appears to be a legitimate URL.
“Since the URL isn’t visible within the body text, it is easy to miss at first glance,” the researchers write. “The first link redirects to a real survey monkey link, and then finally to the landing page of the phishing site....As these emails originated from the legitimate SurveyMonkey email address, and the body of the email contains a link to the real survey monkey domain, one would easily believe the email to be benign. However, it isn’t until the second redirect where the user is led to a phishing page that the attacker controls.”
Additionally, the researchers note that the phishing email prepares the user to believe they may be asked to enter their credentials to verify their identity.
“Because the email mentions that each survey link is unique to each recipient of the email, users may be primed to think that the login page is there to validate that their responses are from the legitimate recipient of the email,” the researchers say. “Thus, the behavior isn’t unexpected (even if it’s atypical – recipients should never enter their email credentials into a survey, regardless of which service is providing it).”
New-school security awareness training can teach your employees to be suspicious whenever they’re asked to enter their credentials, even if they initially think they’re on a legitimate site.
 Here's how it works:
Here's how it works:




