 Microsoft’s recent posts detailing a new Java attack that uses PowerShell and other legitimate tools to infect victims with ransomware sheds light on human-operated attacks.
Microsoft’s recent posts detailing a new Java attack that uses PowerShell and other legitimate tools to infect victims with ransomware sheds light on human-operated attacks.
According to Microsoft’s Advanced Threat Analytics, the median number of days an attacker sits within your network undetected is 146 days. This new PonyFinal ransomware demonstrates this behavior. According to Microsoft, attackers in this case put a human touch on the attack, not leveraging automation, but are patient and are looking for victims of opportunity rather than trying to hit everyone and anyone.
By first compromising internet-facing web systems, attackers compromise privileged credentials and use PowerShell tools and service accounts to obtain the needed access the victim network. In most cases, the attackers focus on endpoints where the Java Runtime Environment (JRE) is installed Then, according to Microsoft, attackers “stay dormant and wait for the most opportune time to deploy the [PonyFinal] payload.”
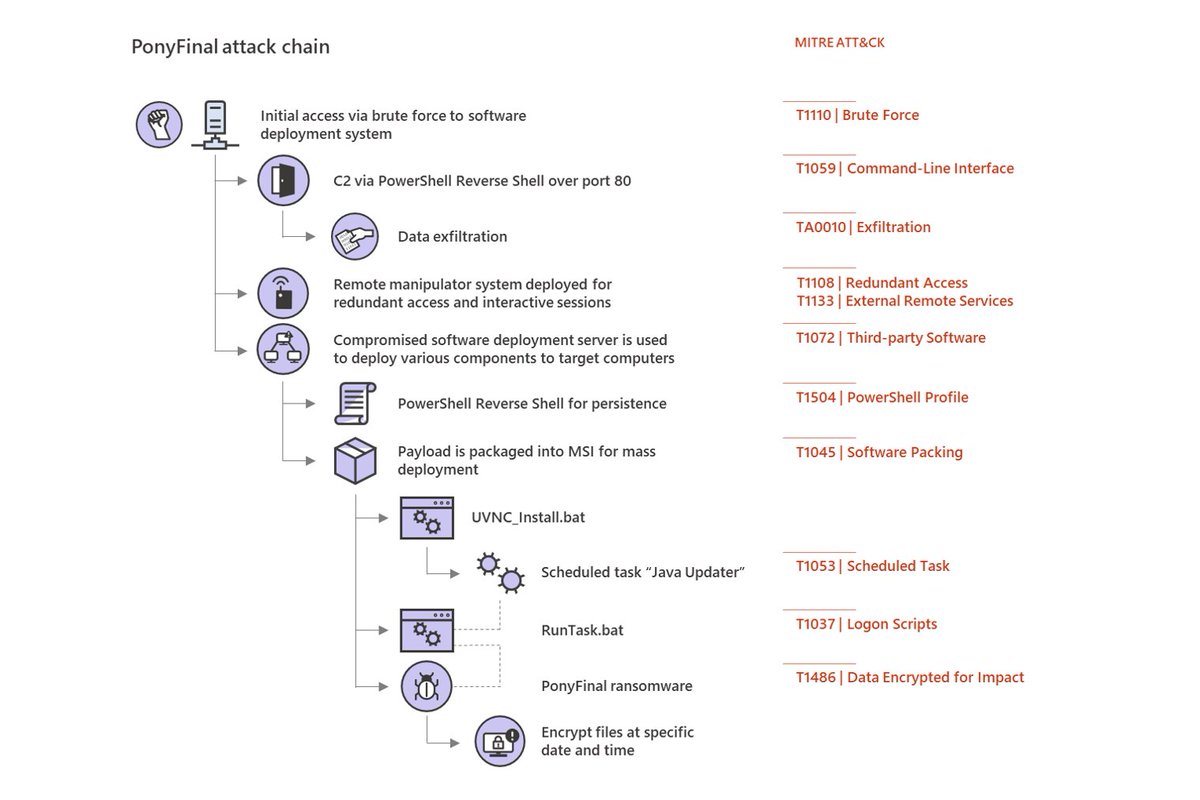
Microsoft recommends a layered security approach that includes both proactive and reactive protective measures. We’ll add that in cases where the initial attack vector is phishing, shoring up the user’s sense of security via Security Awareness Training is critical to avoid the installation of Trojans and other types of malware that will eventually download a ransomware payload.
 Here's how it works:
Here's how it works:




