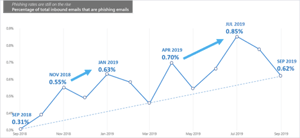
According to Microsoft security research, the percentage of inbound emails associated with phishing on average increased in the past year. For some, this may feel like obvious news, but given the scale of Microsoft and their visibility into global traffic, the security intelligence report makes for some interesting fact-based reading.
Souce: Microsoft Security Intelligence Report
According to a blog penned by Microsoft Cybersecurity Field CTO Diana Kelley, many criminals are taking the time to research victims before attacking, leading to more targeted spear phishing attacks including business email compromise (BEC), wire / W2, and impersonating high profile accounts.
Microsoft recommends a layered approach, using technology to secure identities such as multi-factor authentication (MFA) as well as deploying spoof detection controls. But underpinning this are the users:
“Spear phishing emails do a great job of effectively impersonating a credible source; however, there are often small details that can give them away. Help users identify phish using training tools that simulate a real phish. Here are a few tells that are found in some phish that you can incorporate into your training:
- An incorrect email address or one that resembles what you expect but is slightly off.
- A sense of urgency coupled with a request to break company policy. For example, fast tracking payments without the usual checks and procedures.
- Emotive language to evoke sympathy or fear. For example, the impersonated CEO might say you’re letting them down if you do not make the urgent payment.
- Inconsistent wording or terminology. Does the business lingo align with company conventions? Does the source typically use those words?”
Further recommendations state that its important that users flag phishing emails to the proper team.
These are all points with which we couldn’t agree more. Security Awareness Training is important to educate users on how to identify suspicious email content and to avoid clicking on attachments. Additionally, phishing testing of your users helps provide a feedback loop for the training, helping you identify where your “user security,” as it were, is weakest.
 Here's how it works:
Here's how it works:




