Redmond states the obvious: "Hackers are going for the low-hanging fruit."
Microsoft has just released their Security Intelligence Report (SIR), its annual cybersecurity summary, and it says that phishing is still the most popular way for cyber-criminals to attack, giving security experts everywhere headaches.
To create the report, Microsoft scanned more than 400 billion emails, 450 billion authentications and 1.2 billion devices. More than half (53 per cent) of all email threats are phishing ones. Three quarters (75 per cent) contain a malicious URL. Here is the upshot:
- Hackers in general have diverted their attention to the 'low-hanging fruit'. The SIR describes three of these routes: social engineering, poorly-secured cloud apps, and the abuse of legitimate software platform features.
- Social engineering attacks are largely synonymous with phishing attacks. The SIR notes "a significant volume of phishing-based email messages at the very end of the year 2017. Phishing was the #1 threat vector (> 50%) for Office 365-based email threats in the second half of calendar year 2017." There are various tools available to help detect phishing, but some academics doubt that even machine learning techniques will be unable to solve the problem.
- Microsoft stresses the value of end-user security awareness training. While users are often called 'the weakest link', they are also a critical line of defense. Every well-trained user is effectively an individual human firewall.
“As software vendors incorporate stronger security measures into their products, it is becoming more expensive for hackers to successfully penetrate software. By contrast, it is easier and less costly to trick a user into clicking a malicious link or opening a phishing email,” Microsoft said.
“In 2017 we saw “low-hanging fruit” methods being used such as phishing — to trick users into handing over credentials and other sensitive information. In fact, phishing was the top threat vector for Office 365-based threats during the second half of 2017.”
Second biggest threat are 'leaky cloud apps'. Microsoft says just three per cent of them support HTTP protection methods, while 86 per cent of them do not encrypt data, at all.
“Other low-hanging fruit for attackers are poorly secured cloud apps. In our research, we found that 79 per cent of SaaS storage apps and 86 per cent of SaaS collaboration apps do not encrypt data both at rest and in transit.” Here is a link to their PDF with the report.

We've got something really cool for you: the new Phishing Security Test v3.0!
Sending simulated phishing emails is a fun and an effective cybersecurity best practice to patch your last line of defense… your users.
Find out the Phish-prone percentage™ of your organization with our free updated Phishing Security Test that now includes our New Industry Benchmarking. See where you stack up! Industry Benchmarking enables you to compare your organization’s Phish-prone percentage with others in your industry.
Find out how you are doing compared to your peers and see the difference 12 months can make after using the integrated KnowBe4 Simulated Phishing and Security Awareness Training platform!
With Our Updated Phishing Security Test: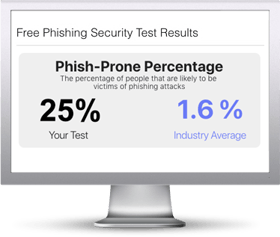
- You can customize the phishing test based on your environment
- Choose the landing page your users see after they click
- Show users which red flags they missed, or a 404 page
- Get a PDF emailed to you in 24 hours with your Phish-prone % and charts to share with management
- See how your organization compares to others in your industry
The Phish-prone percentage is usually higher than you expect and is great ammo to get budget.
Start phishing your users now. Fill out the form, and get started immediately. There is no cost.
PS: Don't like to click on redirected buttons? Cut & Paste this link in your browser:





