Microsoft Office documents containing malicious macros accounted for 45 percent of malware loaders in August 2018, according to a blog post by Cofense. These macros were used to deliver a wide range of different types of malware, showing that this method is a universal top choice for both sophisticated and amateur attackers.
The popularity of Microsoft Office documents as a malware delivery mechanism stems from their lack of safeguards to prevent a file from executing code. Macros are either enabled by default or can be activated with a single click once the document is opened. This is generally the first stage of an infection, as the macro will then download malware from a remote server.
The best way to defend against this threat is to either disable macros for the entire organization or to block documents at the gateway. The Cofense researchers note, however, that these solutions would drastically reduce the productivity of most companies. Therefore, they recommend a combination of strong security systems and ample user education.
While malware poses a severe threat to organizations, social engineering as a whole is far more widespread. Researchers at FireEye found that one out of every one hundred emails is malicious, and 90 percent of those email attacks do not contain malware. Instead, they use social engineering tactics to trick the victim into sharing sensitive information directly with the attacker.
Employees need new-school security awareness training to prepare them for these threats before they fall victim to real attacks. Infosecurity Magazine has the story: https://www.infosecurity-magazine.com/news/microsoft-office-macros-still-no-1/
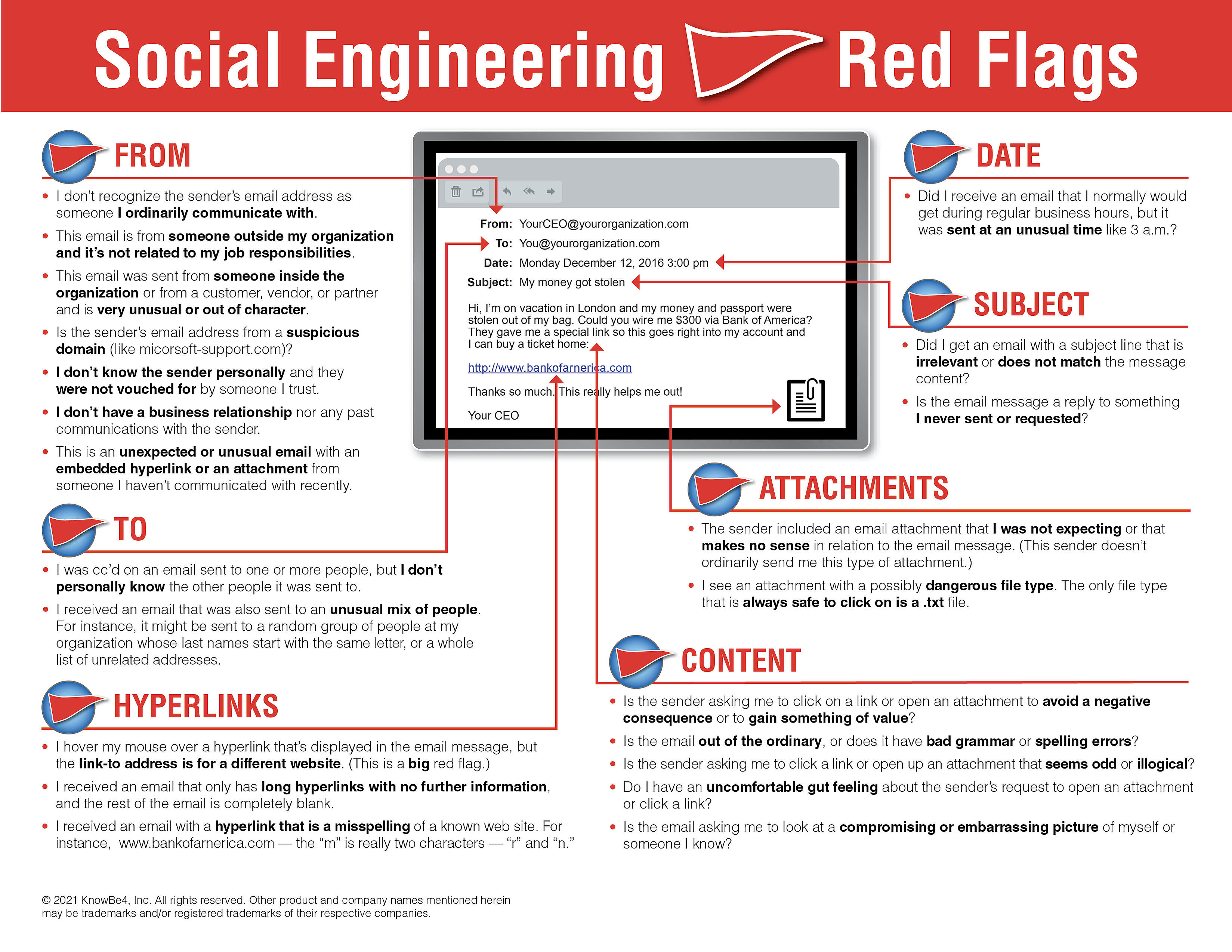
We recommend EVERYONE to review the 22 social engineering red flags to watch out for in any email. It might be a good idea to print out this PDF and pass it along to family, friends, and coworkers.