 Threat actors are using a couple of dangerous, new tactics to exploit the so-called ProxyShell set of vulnerabilities in on-premises Exchange Servers that Microsoft patched earlier this year — and were the targets of widespread attacks in July.
Threat actors are using a couple of dangerous, new tactics to exploit the so-called ProxyShell set of vulnerabilities in on-premises Exchange Servers that Microsoft patched earlier this year — and were the targets of widespread attacks in July.
In multiple recent incident response engagements, Mandiant researchers found attackers had abused ProxyShell to drop Web shells on vulnerable systems in a different — and more difficult to detect — manner than used in previous attacks. In some attacks, threat actors skipped Web shells entirely and instead created their own hidden, privileged mailboxes, giving them the ability to take over accounts and create other problems.
As many as 30,000 Internet-facing Exchange Servers remain vulnerable to these attacks because they have not been patched, Mandiant said. Full article at DarkReading.
Cancel
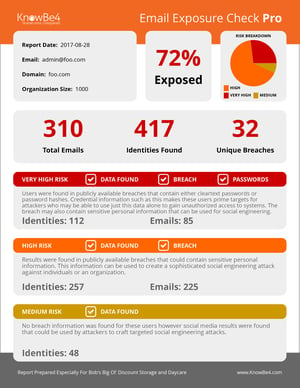 Here's how it works:
Here's how it works:




