 New data from CheckPoint identifies those brands being used by threat actors to trick victims into opening attachments, clicking links, providing credentials, and giving up personal details.
New data from CheckPoint identifies those brands being used by threat actors to trick victims into opening attachments, clicking links, providing credentials, and giving up personal details.
The use of a familiar brand has long been a tactic used by cybercriminals in an effort to elevate the credibility of an email, to lower the defenses of the potential victim, and to get said victim to engage with the phishing email in the desired manner.
According to the latest data from security vendor CheckPoint in their Brand Phishing Report Q2 2021 blog, Microsoft is the predominate brand used in phishing attacks by a wide margin:
- Microsoft (45%)
- DHL (26%)
- Amazon (11%)
- Best Buy (4%)
- Google (3%)
In addition, the cybercriminals are getting pretty good at crafting realistic-looking emails that feel like they are really from the brands they claim. The email below provided by CheckPoint is one great example:
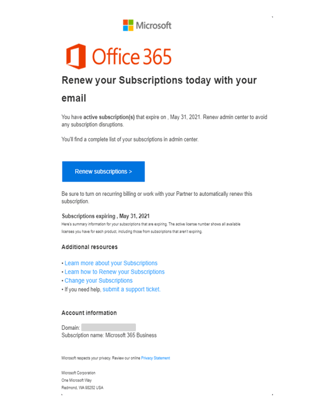
Source: Checkpoint
Note how it seems to have a look and feel that passes muster and could be misconstrued as being legitimate.
Your only real defense is to elevate your user’s sense of vigilance – the red flags should be going up first because this kind of email is unexpected and then the email’s contents should be scrutinized (e.g., the email’s subject reads “Your Subscription Has Been Expired” which obviously reads a bit odd). By placing users into continual Security Awareness Training, users can be taught to keep a watchful eye out for suspicious or unexpected emails, regardless of what brand is used.
 Here's how it works:
Here's how it works:




