 Taking advantage of the value of a legitimate web service, along with a valid SSL certificate, a new campaign of phishing attack targeting online Microsoft credentials is leveraging Azure.
Taking advantage of the value of a legitimate web service, along with a valid SSL certificate, a new campaign of phishing attack targeting online Microsoft credentials is leveraging Azure.
Microsoft Azure’s App Service empowers organizations to quickly create and deploy web-based apps. But a new use for this service was recently identified by the analysts at MalwareHunterTeam. On their Twitter account (shown below), they posted the finding of a set of threat actors using the service’s legitimacy to help get malicious content focused on stealing OneDrive, Microsoft 365, Outlook.com, Rackspace, Aol, and any other online mail platform’s credentials.
Did you heard about "Azure Static Web Apps" yet? If no, let me explain to you in short what is that: it is another service from Microsoft for actors to help them phish their own customers / users...
— MalwareHunterTeam (@malwrhunterteam) March 30, 2022
😂
😫
A fresh example: https://agreeable-dune-0b7a9100f.1.azurestaticapps[.]net/ pic.twitter.com/gwf7YdG3Fx
These attacks likely work in conjunction with a phishing attack that gets the victim to want to see the contents of a weblink, and then – using realistic spoofed logon pages – asks the victim to “logon” to steal their credentials.
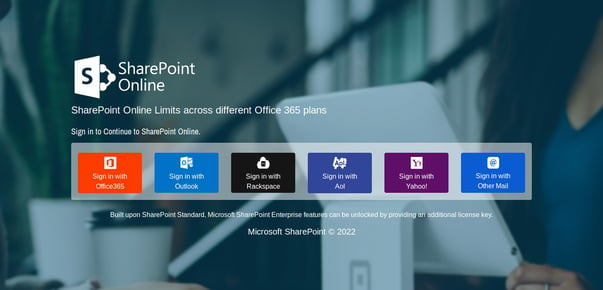
These kinds of attacks are relatively simple to spot, if the user in question has undergone continual Security Awareness Training that not only educates them on tactics like the ones used in this attack, but also elevates their sense of awareness so they will scrutinize a logon page like the one above and quickly come to the same conclusion that every IT pro does instantly when seeing it – it’s a scam.
 Here's how it works:
Here's how it works:




