 Microsoft released an alert about a new ransomware strain called ZCryptor, which works like a worm and spreads via removable and network drives.
Microsoft released an alert about a new ransomware strain called ZCryptor, which works like a worm and spreads via removable and network drives.
The MalwareForMe blog reported this first on May 24. Three days later, Redmond's security team decided to alert people about this threat. Because the ransomware adds the .zcrypt file extension to locked files, some security researchers also call "zCrypt".
“We are alerting Windows users of a new type of ransomware that exhibits worm-like behavior,” Microsoft's Malware Protection Center alert stated. “This ransom leverages removable and network drives to propagate itself and affect more users.” A subsequent analysis by Trend Micro confirmed Microsoft's findings, categorizing the threat as a "worm," with self-propagation features.
ZCryptor spreads via phishing emails with malicious macro attachments and a fake Flash Player installer
Microsoft wrote that this strain use fake installers, usually for Adobe Flash, along with macro-based booby-trapped Office files to distribute the Zcryptor ransomware. Macro-based malware uses what could be argued as "user-consent prompt fatigue". Only Microsoft can come up with a term like that.
Once the user installs the fake Adobe Flash update or allows an Office file to run macros, the Zcryptor ransomware is installed on the user's computer. The first thing the ransomware does is to gain PC restart persistence by adding a key to the computer's registry. It also drops in files to autorun and hide itself in the file explorer. After this, it starts to encrypt files and add the .zcrypt extension to infected files.
Based on samples it analyzed, Microsoft reported the ransomware was targeting 88 different file types. The security researcher MalwareHunterTeam told Softpedia that, in samples he analyzed, he saw the ransomware targeted 121 different file types, so it appears that ZCryptor's authors are still working and adding new code.
ZCryptor apparently is able to copy itself to removable and network drives
The most worrying thing was Microsoft saying the ransomware has "worm-like behavior," meaning it can spread by itself to nearby targets. This type of behavior was predicted, but now it's here. This is one of the first ransomware strains that features such a function. MalwareHunterTeam also said "that it [ZCryptor] has the codes to copy itself to removable devices."
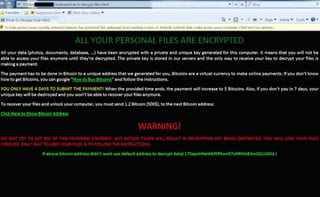
Once embedded and the files are encrypted a ransom note appears demanding 1.2 bitcoins, around $500, for the decryption key. It gives the victim four days to comply and then boosts the payment to five Bitcoins ($2,200)
Ransomware Hostage Rescue Manual
Get the most complete Ransomware Manual packed with actionable info that you need to have to prevent infections, and what to do when you are hit with ransomware.

Don't like to click on redirected buttons? Cut & Paste this link in your browser:
https://info.knowbe4.com/ransomware-hostage-rescue-manual-0




