 In a step towards educating customers on why attachments and URLs are deemed “malicious”, Microsoft’s is set to augment its Advanced Threat Protection product in July.
In a step towards educating customers on why attachments and URLs are deemed “malicious”, Microsoft’s is set to augment its Advanced Threat Protection product in July.
There are lots of reasons why a security solution comes to a “malicious verdict” when it comes to email content. It could be the URL link in the email points to a site that’s been compromised. Or perhaps it’s that the attachment, when detonated, attempted to install software. In some cases, IT organizations never know – and can’t be better protected through experiential knowledge.
But a new update to Microsoft’s Advanced Threat Protection product will provide customers with details on any malicious behaviors the solution finds when examining and detonating email content.
According to the Microsoft 365 Roadmap entry:
We’re working to reveal more of the details that led to a malicious verdict when URLs or files are detonated in Office 365 ATP. In addition to the detonation chain (the series of detonations that were necessary to reach a verdict for this entity), we’ll also share a detonation summary, with details such as detonation time range, verdict of the file or URL, related entities (other entities called or used during the detonation), screenshots, and more.
This is a huge step in not only demonstrating the effectiveness of Microsoft’s solution, but this also allows organizations to better understand what tactics are being used and how their other security solutions can be used to protect the organization.
This spirit of educating the “why” behind malicious is what Security Awareness Training is all about; by teaching IT and users what tactics are being used, everyone’s understanding of attacks and the need for vigilance is elevated, only helping to improve the organization’s security stance.
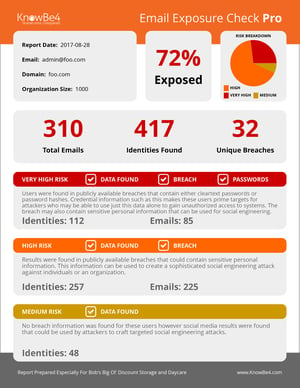 Here's how it works:
Here's how it works:




