 As the aftermath unfolds, the details around the recent attack on MGM Resorts provides crucial insight into the attacks impact, who’s responsible, and how it started.
As the aftermath unfolds, the details around the recent attack on MGM Resorts provides crucial insight into the attacks impact, who’s responsible, and how it started.
On September 11, Las Vegas-based MGM Resorts International reported a cybersecurity “issue” affecting many of the company’s systems. A report with the Securities and Exchange Commission was filed on September 12, denoting the issue was severe enough to inform law enforcement and taking measures including “shutting down systems.” It was later determined that a ransomware attack had occurred, affecting the company’s website, reservation systems, key card systems, and more.
According to the Wall Street Journal, half of a $30 million dollar ransom was paid to those behind the attack. There is some confusion as to who is responsible for this attack. Early on, a tweet by vx-underground attributed the attack to the ALPHV ransomware gang. But others are attributing the attack to a cybercriminal group know as both Scattered Spider and UNC3944 – a group though to be made up of teenagers operating from both the U.S. and the U.K. They reportedly encrypted more than 100 MGM ESXi hypervisors.
But the more immediate issues are how did this even happen and – given this is a ransomware attack, which likely includes data exfiltration and extortion – was there any data stolen?
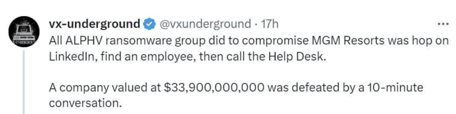
According to the previously-mentioned tweet by vx-underground, it’s believed that simple social engineering and a password reset call to the helpdesk was the cornerstone of the attack. Compromising a single account is more than enough of a foothold to spread malware via email and potentially log onto a virtual, remote, or even on-premises endpoint.
A second SEC filing by MGM Resorts parent company, Caesars Entertainment, provides some insight into what kind of data was accessed and potentially stolen; the threat actors responsible “acquired a copy of, among other data, our loyalty program database, which includes driver’s license numbers and/or social security numbers for a significant number of members in the database.” From the filing, it appears that the paid ransom was made to “ensure that the stolen data is deleted by the unauthorized actor.”
Given that the individuals in the loyalty program are those that spend money (which includes high rollers), it’s fairly likely that those individuals will become targets themselves of social engineering attacks in an attempt to get them to part with thousands or even millions of dollars themselves.
The complete outcome of this attack remains to be seen. In just 3 days, we have so much detail that paints a devastating picture for MGM. The next few weeks will provide more clarity on just how impactful this attack was.
All it took to cost MGM millions was 10 minutes worth of rudimentary social engineering. Think about that for a moment. Putting strict processes in place around updating of credentials, the use of multi-factor authentication for every single user, and putting every employee through Security Awareness Training are needed steps to significantly reduce the risk of a successful initial attack that will act as the foothold for a larger one like that of MGM Resorts.
 This 26-page manual is packed with actionable info that you need to prevent infections, and what to do when you are hit with ransomware. You also get a Ransomware Attack Response Checklist and Prevention Checklist. You will learn more about:
This 26-page manual is packed with actionable info that you need to prevent infections, and what to do when you are hit with ransomware. You also get a Ransomware Attack Response Checklist and Prevention Checklist. You will learn more about:




