SecurityAffairs just published a new discovery that you need to know about. A Brazilian Infosec research group, Morphus Labs, just discovered a new Full Disk Encryption (FDE) ransomware strain this week, dubbed “Mamba”, a snake with a paralyzing poison.
Mamba, just like Petya, uses a disk-level encryption strategy instead of the conventional file-based one. Full-disk encryption seems to be a new ransomware trend.
About Mamba
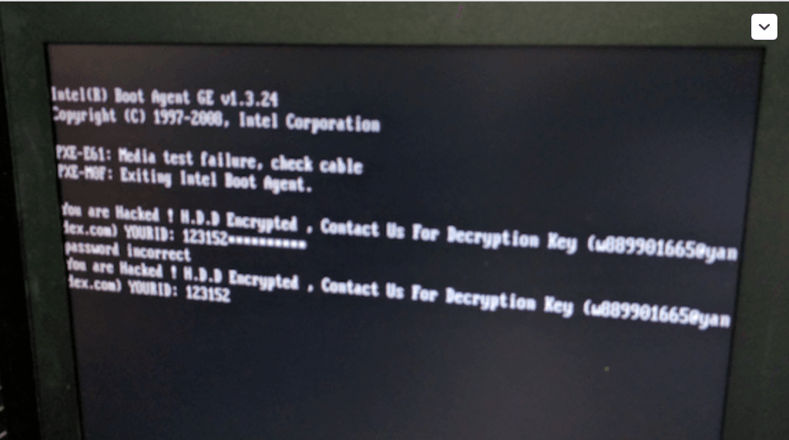
“You are Hacked”. This message is all that remains of the victims of this new ransomware. To get the decryption key, victims must contact somebody through the e-mail address given in the message, give their unique ID and pay 1 BTC (currently ~$600) per infected host.
Petya encrypts the master file table (MFT) and not the data itself. But Mamba differs from Petya; it uses a full disk encryption open source tool called DiskCryptor to strongly encrypt all the data on the machine's hard drive. Morphus Labs discovered Mamba while responding to an incident that infected a company's servers in Brazil, the United States and India.
This ransomware strain blocks the OS from even booting up. It overwrites the boot disk master boot record (MBR) with a custom one that displays the ransom message on the screen and asks for the decryption password like you can see in the picture above.
Once the malware is introduced on a machine, it will reboot. Before the reeboot, Mamba installs itself as a fake defragmentation Windows service. See the full technical details from Renato Marinho at Morphus Labs.
The infection vector for Mamba is unknown at this point, although it's likely being spread through phishing emails. Yet another reason why you ALWAYS need to think before you click. It's also a good idea to make sure your users have security awareness training so your network doesn't get infected with damaging ransomware.
KnowBe4's integrated training and phishing platform allows you to send fully simulated phishing scams so you can see which users answer the emails and/or click on links in them or open infected attachments.
See it for yourself and get a live, one-on-one demo.
PS: Don't like to click on redirected buttons? Cut & Paste this link in your browser:
https://info.knowbe4.com/kmsat-request-a-demo





